CERT/CC launches Twitter bot to give security bugs random names

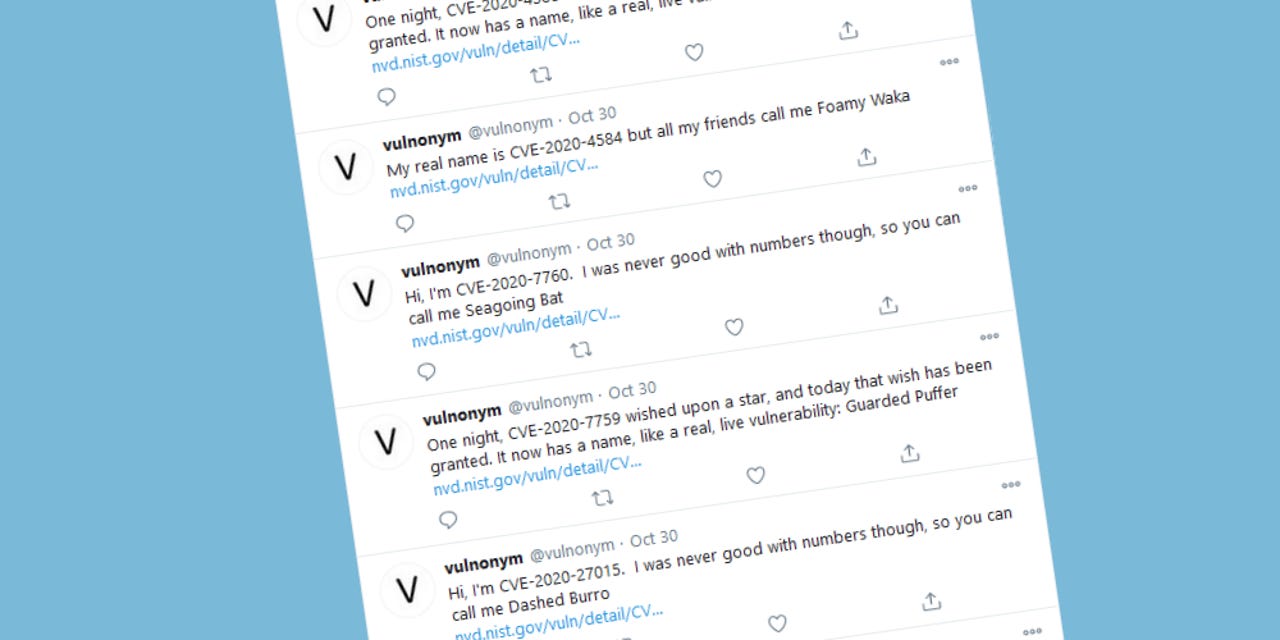
In an attempt to reduce the use of sensationalized and scary vulnerability names, the CERT/CC team launched a Twitter bot that will assign random and neutral names to every security bug that receives a CVE identifier.
Named Vulnonym, the bot is operated by the CERT Coordination Center (CERT/CC) at the Carnegie Mellon University, the first-ever CERT team created, and now a collaborator and partner of the DHS' official US-CERT team.
The idea for this bot came after the seemingly unending discussions around the topic "if vulnerabilities should have names?"
The problem with vulnerability names
For decades, all major security flaws have been assigned a CVE identifier by the MITRE Corporation. This ID is usually in the format of CVE-[YEAR]-[NUMBER], such as CVE-2019-0708.
These CVE IDs are usually used by security software to identify bugs, track, and monitor bugs for statistical or reporting purposes, and CVE IDs are rarely used by humans in any meaningful way.
Over the years, some security firms and security researchers realized that their work in identifying important bugs could easily get lost in a constant stream of CVE numbers that almost everyone has a hard time remembering.
Companies and researchers realized that the bugs they discovered had more chances to stand out if the bug had a cool-sounding name.
And so the practice of "bug naming" came to be, with the best-known examples being Spectre, Meltdown, Dirty Cow, Zerologon, Heartbleed, BlueKeep, BLESA, SIGRed, BLURTooth, DejaBlue, or Stagefright.
But as time went by, some vulnerability names started to deviate from being descriptive of a security bug and entered the realm of fearmongering and attention-seeking, becoming a marketing shtick.
Things reached a ridiculous level last year when a Cisco bug was named using three cat emojis under the spoken term of Thrangrycat (aka "three angry cats").
For the past years, many security experts have started to react with vitriol and derision every time a security bug is disclosed, and the bug has a name.
Some major bugs have been played down just because the vulnerability received a name, while seemingly unexploitable bugs were overhyped and received way too much media attention just because they were launched with a name, website, logo, and sometimes even with theme songs.
Yes, vulnerabilities should have names
But in a blog post on Friday, the CERT/CC team decided to put forward a solution to put some order in vulnerability naming. Their answer was the Vulnonym bot, which will assign a two-word codename in the format of adjective-noun to every newly assigned CVE ID.
"Not every named vulnerability is a severe vulnerability despite what some researchers want you to think," said Leigh Metcalf, a member of the CERT/CC team.
"We aren't arguing that vulnerabilities shouldn't have names, in fact, we are encouraging this process!"
Metcalf argues that humans inherently need easy-to-remember terms to describe security bugs because "humans aren't well conditioned to remember numbers," such as the ones used for CVE IDs.
She likened the situation to how domain names came to be, as humans are most likely to remember google.com instead of a four-digit IP address where the google.com website is hosted.
"Our goal is to create neutral names that provides a means for people to remember vulnerabilities without implying how scary (or not scary) the particular vulnerability in question is," Metcalf said.