Apple has patched a potent chain of iOS zero-days that were used to infect the iPhone of an Egyptian presidential candidate with sophisticated spyware developed by a commercial exploit seller, Google and researchers from Citizen Lab said Friday.
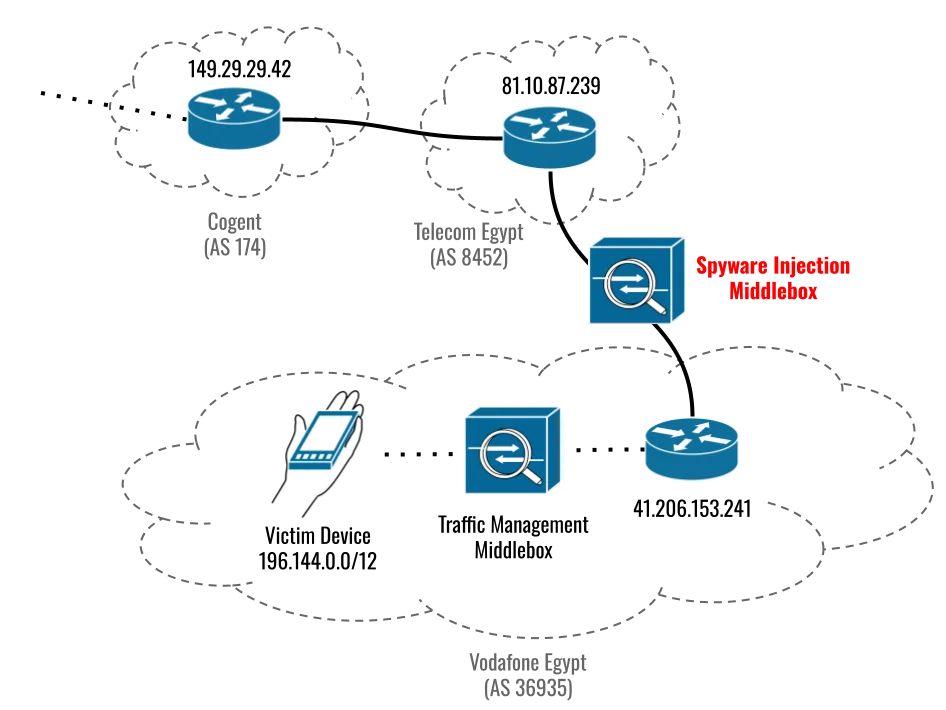
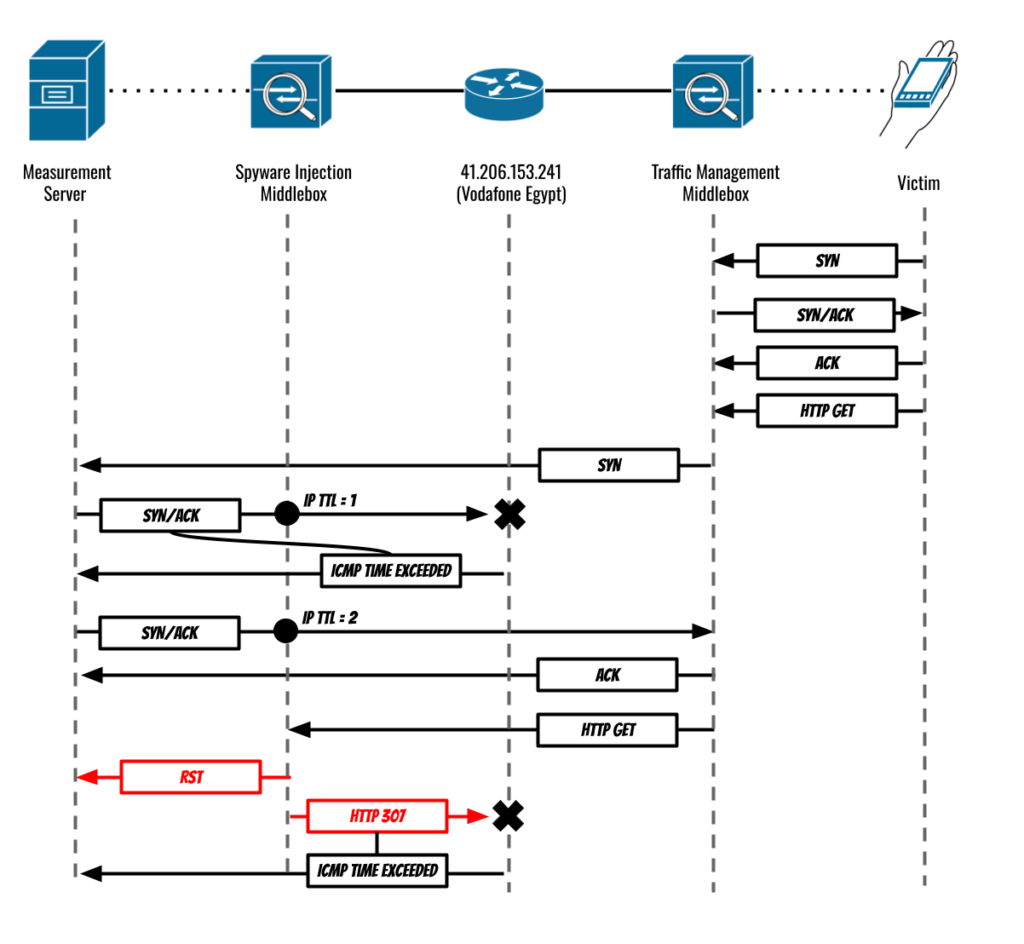
The previously unknown vulnerabilities, which Apple patched on Thursday, were exploited in clickless attacks, meaning they didn’t require a target to take any steps other than to visit a website that used the HTTP protocol rather than the safer HTTPS alternative. A packet inspection device sitting on a cellular network in Egypt kept an eye out for connections from the phone of the targeted candidate and, when spotted, redirected it to a site that delivered the exploit chain, according to Citizen Lab, a research group at the University of Toronto’s Munk School.
A cast of villains, 3 0-days, and a compromised cell network
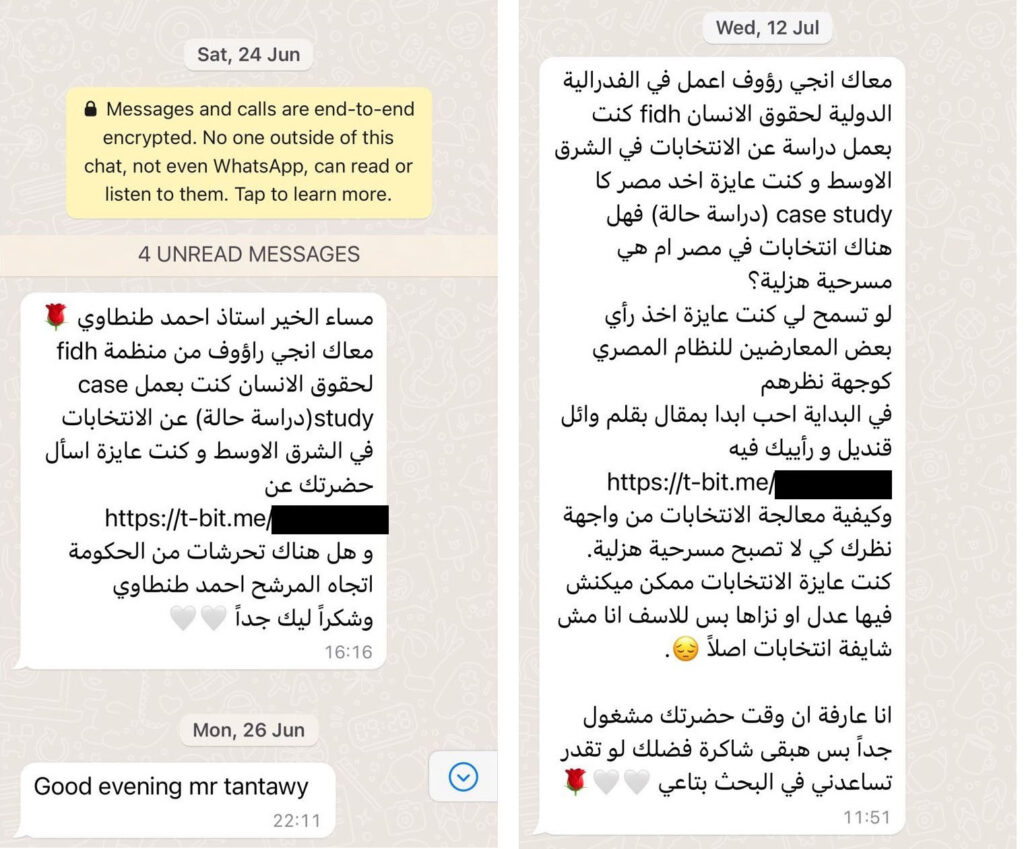
Citizen Lab said the attack was made possible by participation from the Egyptian government, spyware known as Predator sold by a company known as Cytrox, and hardware sold by Egypt-based Sandvine. The campaign targeted Ahmed Eltantawy, a former member of the Egyptian Parliament who announced he was running for president in March. Citizen Lab said the recent attacks were at least the third time Eltantawy’s iPhone has been attacked. One of them, in 2021, was successful and also installed Predator.
“The use of mercenary spyware to target a senior member of a country’s democratic opposition after they had announced their intention to run for president is a clear interference in free and fair elections and violates the rights to freedom of expression, assembly, and privacy,” Citizen Lab researchers Bill Marczak, John Scott-Railton, Daniel Roethlisberger, Bahr Abdul Razzak, Siena Anstis, and Ron Deibert wrote in a 4,200-word report. “It also directly contradicts how mercenary spyware firms publicly justify their sales.”



 Loading comments...
Loading comments...
