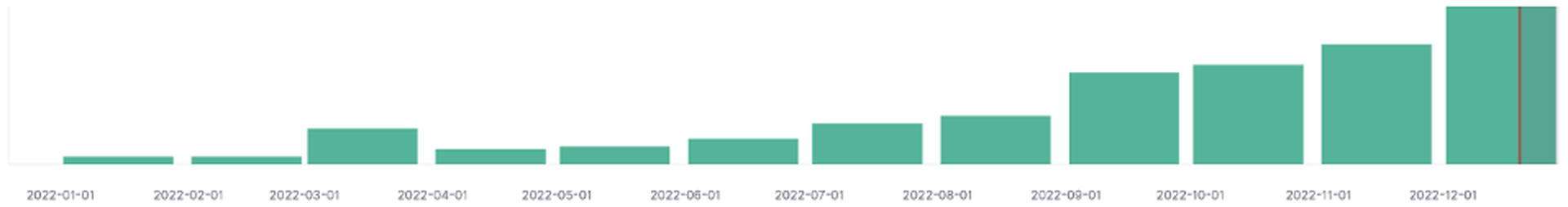
The use of Telegram bots for credential exfiltration increased more than eight-fold between 2021 and 2022, according to new research.
A report released this week by Cofense finds that while Telegram bots being used to exfiltrate information is not new, it has not been commonly used by threat actors in the past for credential phishing. Researchers noted that the significant increase is primarily associated with the current popular tactic of using HTML attachments as delivery mechanisms and the ease of Telegram's setup.
"During 2022, there has been a gradual increase of evasive campaigns using Telegram bots reaching inboxes. Most of the emails in these campaigns contain an attached HTML file. This HTML file generally has a Telegram bot's authentication and location hardcoded and obfuscated, or redirects to a domain that hosts a phishing kit with the bot's ID hardcoded into its resources," the report read.
Telegram bots are like the classic service robots in science fiction movies, but virtual and active on Telegram, Joe Gallop, cyber threat intelligence manager at Cofense explained to SC Media in an interview. Indeed, by the official definition on the Telegram website, these bots can support "any kind of task or service," with some popular functions including delivering answers to users' FAQs, converting certain file types into others, or setting reminders for users.
Unfortunately, "any kind of task or service" also attracts threat actors to perform malicious tasks and services. To exfiltrate phishing information, the only task a bot needs to do is to receive text submitted by the victim and convey it to the threat actor via Telegram chat, the report noted.
Indeed, the procedures for threat actors to set up bots and perform malicious activities only require three simple steps with little cost.
First, following Telegram's official guidance on bot creation, threat actors create bots by messaging the BotFather on Telegram.
Second, they use the Telegram bot's unique API endpoint (https://api[.]telegram[.]org/getUpdates) to get the chat ID, an identifier of chat sessions between the bot and an individual user or multiple users operating in a group chat. The bot will convey stolen credentials in this chat.
Third, threat actors insert the Telegram bot token and chat ID into malicious scripts, programs, or files used in phishing campaigns.
The screenshot below shows an example that Cofense provides of a credential entry form in a malicious HTML file delivered by email. "The HTML file would have a bot's token and chat ID hardcoded in, for authenticating to the Telegram bot's API and delivering the stolen information to the correct location. It also shows the final results being conveyed to the chat between the bot and threat actor," the report said.

Jeremy Fuchs, cybersecurity researcher and analyst at Avanan, said that using Telegram bots in credential phishing is a clever way to avoid detection.
"Utilizing HTML files to obfuscate malicious intentions is not new and remains a popular tactic because it makes deep analysis by security services difficult. We've seen threat actors use JavaScript, HTML entities, custom CSS and more to evade detection. Utilizing Telegram bots is a clever way of doing this, especially since the usage of a bot wouldn't necessarily be visible on the first analysis," Fuchs told SC Media.
However, this sharp increase in the abuse of Telegram bots will also catch the security team's attention, so the success rate of this type of attack is unclear, said Partick Harr, CEO at SlashNext.
SC Media has reached out to Telegram on whether the company has been aware of the issue and has taken any actions accordingly.
As for businesses wanting to protect themselves from Telegram abuse, Gallop recommended that the security team set policies regarding the use of api[.] Telegram [.]org, the domain used by programmers to communicate with bots).
"The details of these policies would likely depend on how much legitimate use of Telegram bots is occurring within an organization. If there is a legitimate usage of Telegram bots within an organization, the organization may allow authorized bot tokens associated with that legitimate usage while blocking other traffic. If it can be confirmed that there is no legitimate usage of Telegram bots within an organization, the organization may block or severely scrutinize all traffic to api[.] Telegram [.]org," Gallop said.
"It is also important for organizations to ensure they have email defenses in place that would prevent the delivery of a credential phishing attack in the first place. This involves developing use more holistic behavioral analysis to identify potential threats rather than relying on static indicators since the characteristics of many credential phishing attacks today, like the abuse of Telegram bots, are much more dynamic and may not be detected using traditional methods," Crane Hassold, director of threat research at Abnormal Security, added.




