
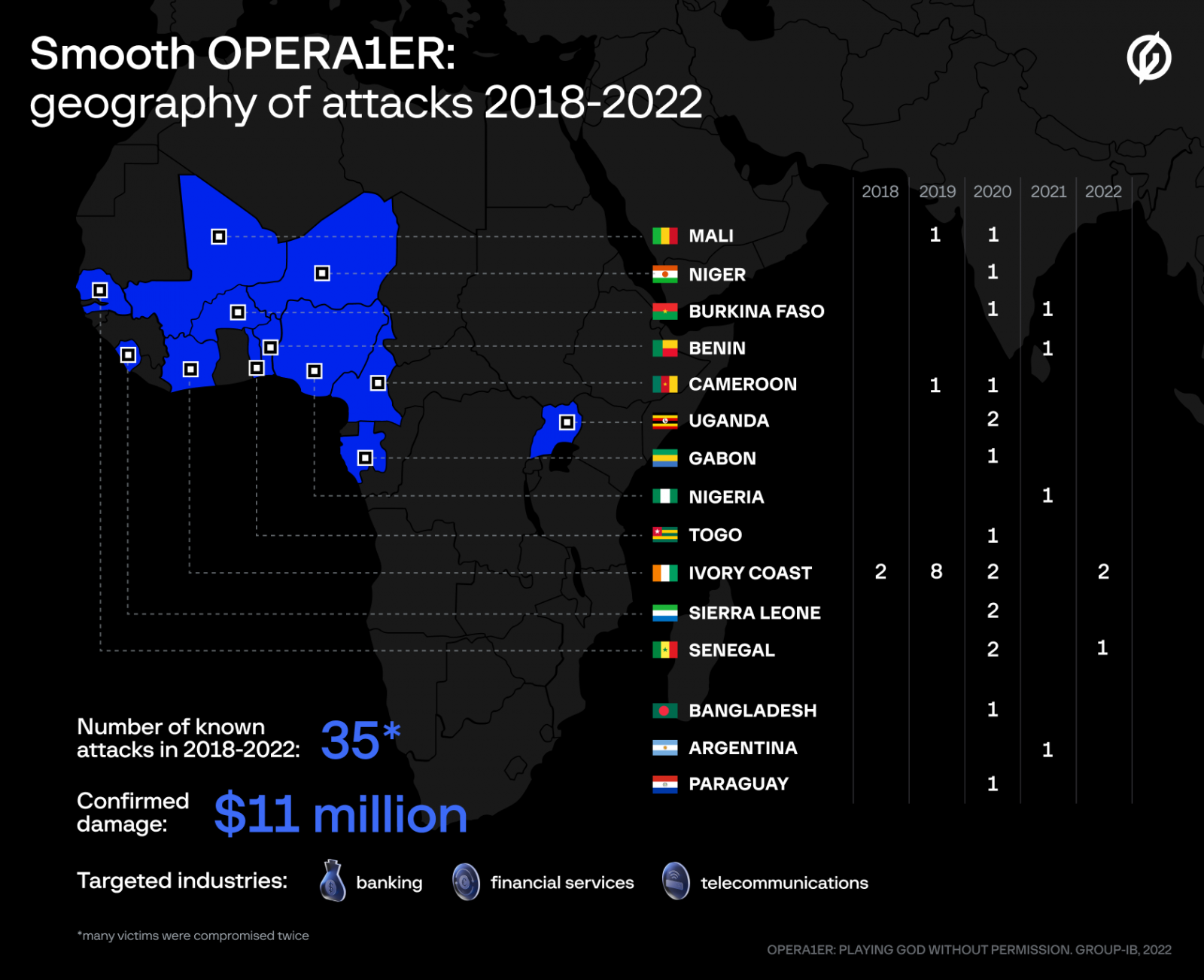
A threat group that researchers call OPERA1ER has stolen at least $11 million from banks and telecommunication service providers in Africa using off-the-shelf hacking tools.
Between 2018 and 2022, the hackers launched more than 35 successful attacks, about a third of them carried out in 2020.
Analysts at Group-IB, working with the CERT-CC department at Orange, have been tracking OPERA1ER since 2019 and noticed that the group changed its techniques, tactics, and procedures (TTPs) last year.
Concerned about losing the threat actor's tracks, the cybersecurity company waited for the group to resurface to publish an updated report. This year, Group-IB observed that the hackers were active once again.
OPERA1ER attack details
The hacker group is formed of French-speaking members believed to operate from Africa. Apart from targeting companies in Africa, the gang also hit organizations in Argentina, Paraguay, and Bangladesh.
OPERA1ER relies on open-source tools, commodity malware, and frameworks like Metasploit and Cobalt Strike to compromise company servers.
They obtain initial access through spear-phishing emails leveraging popular topics like invoices or postal delivery notifications.
The emails have attachments that deliver the first-stage malware, among them Netwire, bitrat, venomRAT, AgentTesla, Remcos, Neutrino, BlackNET, and Venom RAT. Group-IB also says that the hackers distributed password sniffers and dumpers.
According to the researchers, OPERA1ER can spend between three to twelve months inside the compromised networks, and sometimes they attack the same company twice.
The researchers say that after getting access to a victim network, the hackers may also use the infrastructure as a pivot point to other targets.
Group-IB says that the threat actor creates “high-quality” spear-phishing emails that are written in French. Most of the times, the messages impersonate either the government tax office or a hiring agent from the Central Bank of West African States (BCEAO).
.png)
source: Group-IB
Using stolen credentials, OPERA1ER accesses email accounts and performs lateral phishing, studies internal documentation to understand money transfer procedures and protection mechanisms, and carefully plans the final, cashing out step.
Typically, the hackers targeted operator accounts that controlled large amounts of money and used stolen credentials to transfer the funds into Channel User accounts, eventually moving them into subscriber accounts under their control.
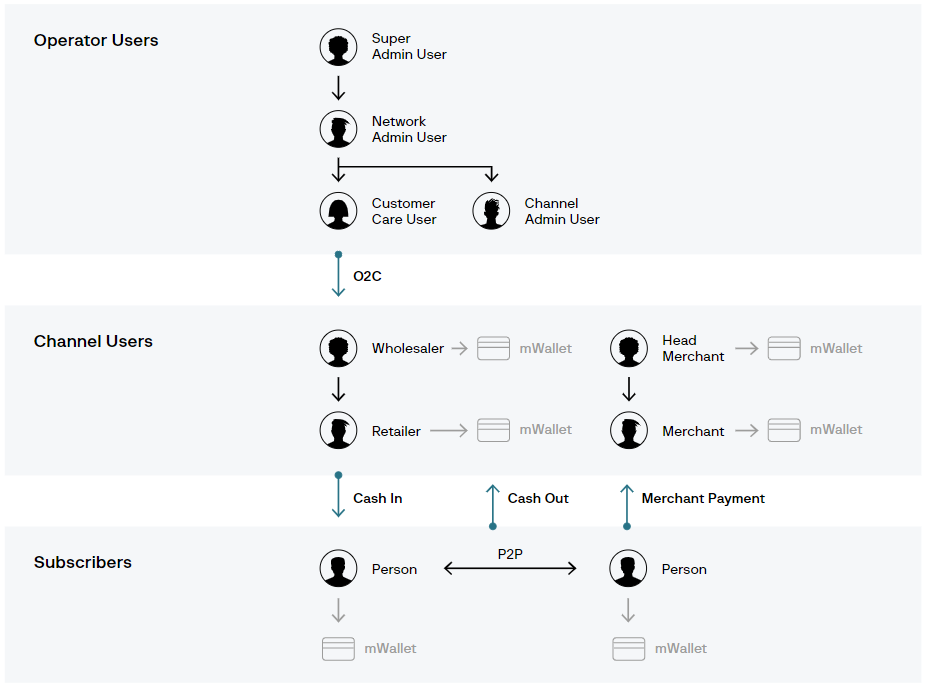
In a report today, Group-IB explains that the gang withdraws the cash via a network of ATMs.
“In one case studied by the researchers, a network of more than 400 subscriber accounts controlled by money mules hired by OPERA1ER was used to enable the cashing out of the stolen funds, mostly done overnight via ATMs” - Group-IB
Usually, the cashing out event took place on a holiday or over the weekend to minimize the chances of the compromised organizations responding to the situation in time.
On victimized banks, OPERA1ER targeted the SWIFT messaging interface software that communicates all details for financial transaction, and siphoned key information about the anti-fraud systems they needed to bypass.
For the complete list of the indicators of compromise (IoCs) and technical details for attacks attributed to OPERA1ER, Group-IB’s has published a 75-page technical report.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now