
Three weeks ago, security researchers exposed a sinister piece of malware lurking inside tax software that the Chinese government requires companies to install. Now there’s evidence that the high-stealth spy campaign was preceded by a separate piece of malware that employed equally sophisticated means to infect taxpayers in China.
GoldenHelper, as researchers from security firm Trustwave dubbed the malware, hid inside the Golden Tax Invoicing software, which all companies registered in China are mandated to use to pay value-added taxes. The malware is able to bypass the User Account Control, the Windows mechanism that requires users to give their approval before software can install programs or make other system changes. Once that’s done, GoldenSpy can install modules with System-level privileges. Trustwave published its findings on Tuesday here.GoldenHelper employs other tricks to conceal its malicious behavior and evade detection from endpoint protection systems and software. The tricks include:
- Randomly generated filenames
- Randomly generated “creation” and “last write” timestamps
- Attempted downloading of executable files using fake filenames with extensions such as .gif, .jpg, and .zip
- Hardcoded logic that uses domain lookup data to control download locations, the content downloaded, and where the content is placed
- Use of an IP-based domain-generation algorithm to change command-server locations on the fly
In some cases, banks deploy the Golden Tax software as stand-alone systems. Trustwave said it uncovered reports from several people who said they received computers running Windows 7 Home Edition that had the tax software—and the hidden GoldenHelper—preinstalled.
The discovery comes three weeks after Trustwave exposed GoldenSpy, a piece of advanced spyware company researchers found installed on the network of a large multinational technology company that had just opened offices in China. Like GoldenHelper, GoldenSpy employed the same installation modus operandi—through the Golden Tax Project.
Trustwave said GoldenSpy had been active from April through last month, when the campaign was abruptly shut down following the security firm’s report. GoldenHelper was active from January 2018 until July 2019, a finding that shows that the tax software has been harboring malware for longer than previously known. GoldenHelper was digitally signed using a Windows-trusted certificate issued to NouNou Technologies, a subsidiary of Aisino Corporation, the same company responsible for the tax software with embedded GoldenSpy malware.
The tax software harboring GoldenHelper was produced by a firm known as Baiwang. Baiwang and Aisino are the only two official providers of the invoicing systems. The latest discovery shows that GoldenSpy wasn’t a one-off campaign, but rather one that used at least one other piece of malware over a more extended period of time than previously known.
It’s not clear why GoldenHelper was shut down so abruptly. One guess is that its operators abandoned the project after detection rates jumped, from about three in January 2019 to as many as 29 by March. Below is a timeline that tracks the history of the malware:
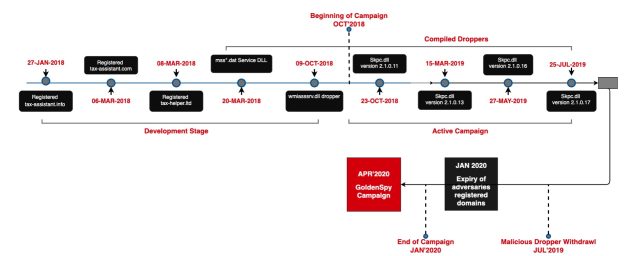
Unlike the investigation into GoldenSpy, Trustwave researchers have yet to find samples of the final payload installed by GoldenHelper. The filename is taxver.exe. Trustwave asks that anyone who can provide a sample reach out to researchers at goldenspy@trustwave.com.
reader comments
102