As the world’s top oil producers prepared for a weeklong meeting earlier this month to plan a response to slumping prices of crude, espionage hackers commenced a sophisticated spearphishing campaign that was concentrated on US-based energy companies. The goal: install a notorious trojan that siphoned their most sensitive communications and data.
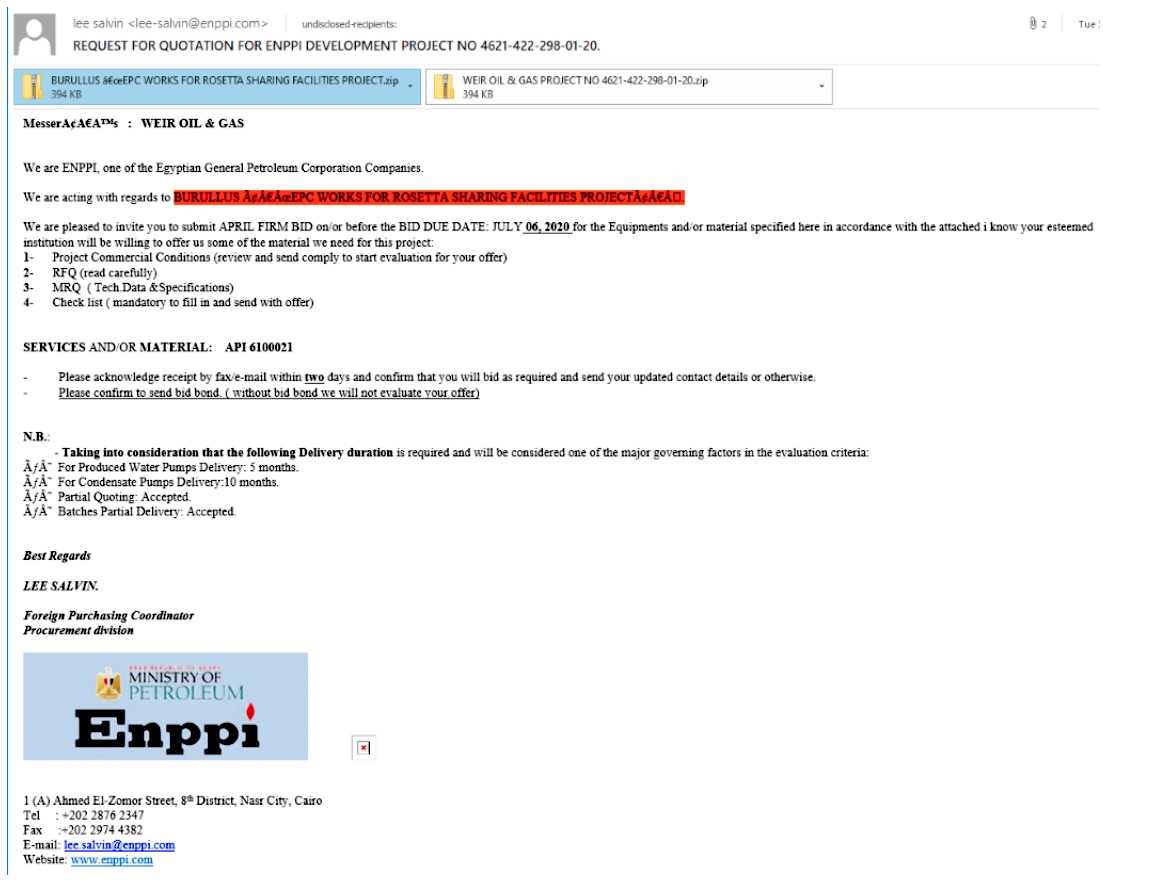
Setting the campaign apart, the emails were mostly free of the typos, broken grammar, and other sloppiness that are typical phishes. The emails also reflected a sender who was well-acquainted with the business of energy production. A barrage of emails that started on March 31, for instance, purported to come from Engineering for Petroleum and Process Industries, a real Egyptian state oil company.
Not your father’s spear-phishing
The sender invited the recipient to submit a bid for equipment and materials as part of a real ongoing project, known as the Rosetta Sharing Facilities Project, on behalf of Burullus, a gas joint venture that’s half-owned by another Egyptian state oil company. The email, which was sent to about 150 oil and gas companies over a week starting on March 31, attached two files that masqueraded as bidding conditions, forms, and a request for proposal. The relatively small number of emails demonstrates a narrow targeting of the carefully crafted campaign. By contrast, many phishing campaigns non-discriminately send tens of thousands of emails.
“To someone in the oil & gas industry, who has knowledge about these projects, the email and the information within might seem sufficiently convincing to open the attachments,” researchers from security firm Bitdefender wrote in a post published on Tuesday.
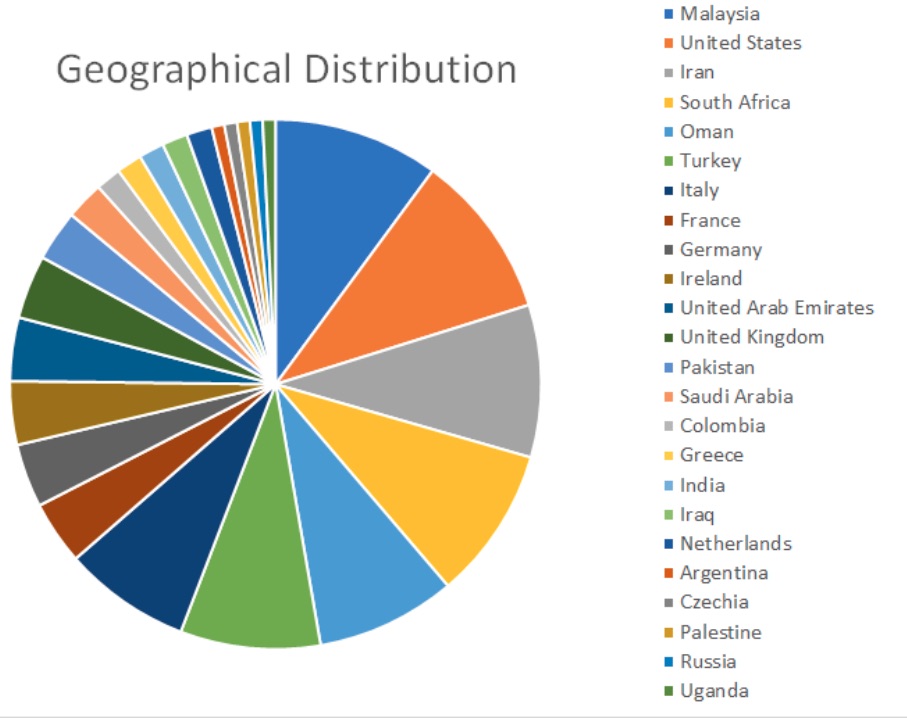
The most-targeted companies were located in Malaysia, the United States, Iran, South Africa, and Oman.
A second campaign started on April 12. It sent an email asking recipients to complete a document known as an Estimated Port Disbursement Account needed for the chemical and oil tanker named MT Sinar Maluku. Not only was that a real vessel registered under the Indonesian flag, it had left its port on April 12 and was expected to reach its destination two days later. The email was sent to 18 companies, 15 of which were shipment companies in the Philippines.



 Loading comments...
Loading comments...
