The TrickBot malware, known previously for targeting U.S. banks, is now setting a bullseye on users of U.S.-based mobile carriers, including Verizon Wireless, T-Mobile and Sprint, to launch SIM swapping attacks.
Researchers with Dell’s Secureworks research team warned that they have observed the malware leveraging a new module that manipulates web sessions for already-infected systems, in order to inject code into websites specifically for U.S. mobile carriers. This code, injected on mobile carrier websites, adds an option on the legitimate websites requesting users’ account PIN number – giving the malware’s operators the ability to steal visitors’ PIN codes and other credentials.
“When a victim navigates to one of these sites from a system infected with TrickBot, the legitimate content will be intercepted and modified,” Keith Jarvis, senior security researcher at Secureworks Counter Threat Unit told Threatpost. He said, modified code is injected into the victim’s browser instead of the legitimate site’s content: “The modifications are typically minor and in this case simply ask for the account PIN during login when normally this is not required by the legitimate site’s login procedure.”
PIN codes are the numeric password codes that must be entered into devices once they are started; therefore, the ability to steal such codes could ultimately give bad actors behind TrickBot the ability to take over victims’ accounts via SIM swapping attacks (also known as “port-out scams”). These scams are where fraudsters use stolen cellular account information to transfer (or “port”) phone numbers to another carrier in order to take control of the phone.
“This fraud allows an attacker to assume control of a victim’s telephone number, including all inbound and outbound text and voice communications,” said researchers on Wednesday. “The interception of short message service (SMS)-based authentication tokens or password resets is frequently used during account takeover (ATO) fraud.”
Web Injection Attacks
Researchers in August observed TrickBot using several dynamic web injection attacks on legitimate websites, including on Verizon Wireless (Aug. 5), T-Mobile (Aug. 12) and Sprint (Aut. 19).
When a victim navigates to the website of one of these organizations, the legitimate server response is intercepted by TrickBot and proxied through a command and control (C2) server.
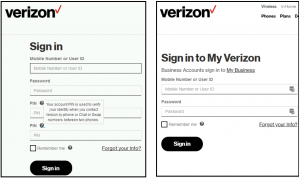
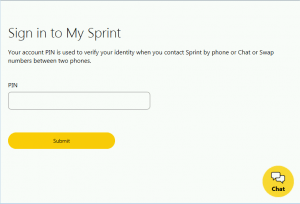
After intercepting network traffic – before it is rendered by a victim’s browser – that C2 server in turn injects additional HTML and JavaScript into the page, which is then rendered in the victim’s web browser. And, for all three carriers, the injected code in this case is an additional form field that requests the user’s PIN code (see the image to the left).
Normally, mobile carriers’ sign in page will only ask for User IDs and passwords. The addition of injected PIN code forms means that in addition to user IDs and passwords, attackers can also siphon victims’ PIN codes.
“The injected code… activates TrickBot’s record (rcrd) functionality,” researchers said. “This functionality creates an additional HTTP request containing the victim’s username, password, and PIN that is transmitted to the TrickBot C2 server. These ‘recordings’ are presented to TrickBot operators as they browse through infected hosts in their web panel.”
TrickBot Evolution
This latest attack marks a rapid departure from TrickBot’s previous targets including U.S. banks.
Since its appearance in 2016, TrickBot has continued to rapidly evolve in both tactics and targeting. Even just in 2019, the malware has switched up its technique to go after remote desktop application credentials and target firms using a tax-themed phishing lure.
Once downloaded, TrickBot typically steals “as much data possible,” researchers said – including banking credentials and more. Researchers note the malware’s new code-injection techniques, updated info-stealing module and a customized redirection method.
Researchers said that in order to mitigate exposure to this malware, organizations should use their available controls to review and restrict access using the indicators of compromise (listed here). They also recommended that organizations use time-based one-time password multi-factor authentication (MFA), as opposed to SMS MFA.
“Similarly, telephone numbers should not be used as password reset options on important accounts,” said researchers. “Enabling a PIN on mobile accounts remains a prudent anti-fraud measure that requires an attacker to possess an additional piece of information about their intended victim.”