
If nation-sponsored hacking was baseball, the Russian-speaking group called Turla would not just be a Major League team—it would be a perennial playoff contender. Researchers from multiple security firms largely agree that Turla was behind breaches of the US Department of Defense in 2008, and more recently the German Foreign Office and France’s military. The group has also been known for unleashing stealthy Linux malware and using satellite-based Internet links to maintain the stealth of its operations.
Now, researchers with security firm Symantec have uncovered evidence of Turla doing something that would be a first for any nation-sponsored hacking group. Turla, Symantec believes, conducted a hostile takeover of an attack platform belonging to a competing hacking group called OilRig, which researchers at FireEye and other firms have linked to the Iranian government. Symantec suspects Turla then used the hijacked network to attack a Middle Eastern government OilRig had already penetrated. Not only would the breach of OilRig be an unprecedented hacking coup, it would also promise to make the already formidable job of attribution—the term given by researchers for using forensic evidence found in malware and servers to pin a hack on a specific group or nation—considerably harder.
A murkier world
“The fact that we’ve seen one advanced group taking over the infrastructure of another nation-backed group changes a lot of policy discussions that are going on, because it complicates attribution,” Jonathan Wrolstad, principal cyber intelligence analyst in Symantec’s Managed Adversary and Threat Intelligence group, told Ars. “This does make us live in the world now that’s a bit murkier.”
Hacking groups go by many different names, depending on the people who track them. Turla is also known as Snake, and Symantec calls it Waterbug. OilRig is also known as APT34, and Symantec calls it Crambus. For consistency, this article will use the names Turla and OilRig.
The hijacking would be only one of Turla’s impressive accomplishments of late. Over the past 18 months, Symantec has observed Turla rolling out a suite of new custom hacking tools, in part to ensure that it regains its signature stealth as previous tools and methods have come to the attention of researchers and rivals. In keeping with a recent trend designed to make detection harder, many of the new tools adopt an approach known as “living off the land,” in which tools run in memory and are based on legitimate administrative tools. New tools rolled out since the beginning of 2018 include:
- A new custom dropper typically used to install Neptun, a backdoor for Microsoft Exchange servers, as a service.
- A custom hacking tool that combines four leaked Equation Group tools (EternalBlue, EternalRomance, DoublePulsar, SMBTouch) into a single executable.
- A USB data collecting tool that checks for a connected USB drive and steals certain file types, encrypting them into a RAR file. It then uses WebDAV to upload to a Box cloud drive.
- Visual Basic scripts that perform system reconnaissance after initial infection and then send information to [Turla] command and control (C&C) servers.
- PowerShell scripts that perform system reconnaissance and credential theft from Windows Credential Manager and then send this information back to [Turla] C&Cs.
- Publicly available tools such as IntelliAdmin to execute RPC commands, SScan and NBTScan for network reconnaissance, PsExec for execution and lateral movement, and Mimikatz (Hacktool.Mimikatz) for credential theft, and Certutil.exe to download and decode remote files. These tools were identified being downloaded via [Turla] tools or infrastructure.
Over the same span, Symantec is aware of Turla compromising 13 organizations, many of them well fortified, in 10 countries. They include:
- The Ministry of Foreign Affairs of a Latin American country
- The Ministry of Foreign Affairs of a Middle Eastern country
- The Ministry of Foreign Affairs of a European country
- The Ministry of the Interior of a South Asian country
- Two unidentified government organizations in a Middle Eastern country
- One unidentified government organization in a Southeast Asian country
- A government office of a South Asian country based in another country
- An information and communications technology organization in a Middle Eastern country
- Two information and communications technology organizations in two European countries
- An information and communications technology organization in a South Asian country
- A multinational organization in a Middle Eastern country
- An educational institution in a South Asian country
Hijacking a rival hacker’s infrastructure
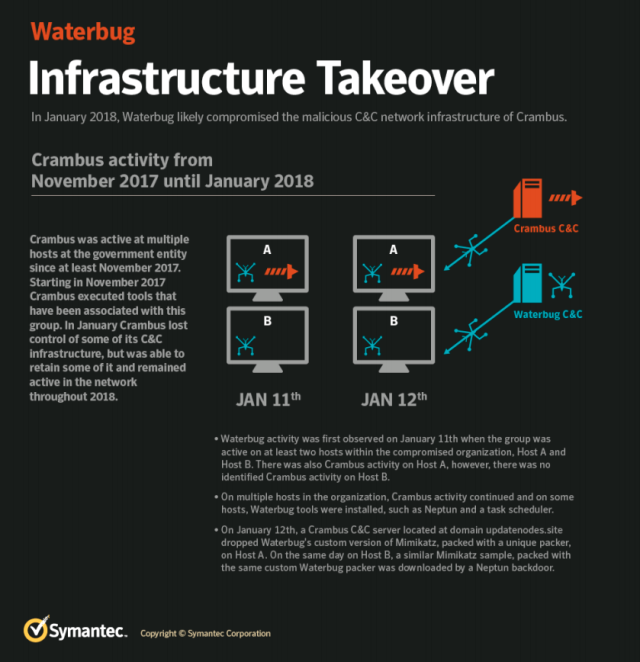
The first compromise of the unidentified Middle Eastern government, Symantec researchers said in a report to be published Thursday, came no later than November 2017, when Symantec security software shows the network was breached by OilRig hackers. Symantec software shows a new breach occurred on January 11, 2018, when a known Turla-linked task scheduling tool named msfgi.exe infected the same network. It’s unusual, but by no means unprecedented, for two nation-sponsored hacking groups to compromise the same network this way.
The next day, Symantec detected evidence of the never-before documented event. It came when an OilRig backdoor called Powruner and an OilRig administration tool called Poison Frog—which had already had access to the Middle Eastern network for months—were used to download a highly customized version of hacking software Symantec researchers believe could only have originated with Turla.
The tool was a heavily customized version of the Mimikatz password extraction tool that was obfuscated using a custom compression routine. Symantec has seen the custom version of Mimikatz and the custom packer used only a handful of times, and each one of them was in campaigns company researchers attributed to Turla.
Symantec believes Turla’s intrusion into the Middle Eastern network continued for most of 2018 in a way that was consistent with other known breaches by the group. In September, for instance, a similar Mimikatz variant was downloaded to another computer on the same network using the Neptun backdoor, which, as noted earlier, Symantec has observed Turla recently started using in its campaigns. Symantec also observed other malware on the Middle Eastern network connecting to known Turla command and control servers.
Symantec researchers can’t rule out the possibility that Turla and OilRig collaborated in the hack of the Middle Eastern network, or even that OilRig somehow obtained its rival's customized version of Mimikatz and the custom packer that obfuscated it. But the researchers discount those possibilities. Turla is an unusually secretive group—even among nation-sponsored hackers. The likelihood of it openly cooperating with a competitor seems slim. What’s more, OilRig has considerably scarcer resources and skills compared to Turla. Not only does that mean Turla would have little to gain from an alliance, it also makes it extremely remote OilRig would have the ability to obtain its larger rival's tools.
Symantec has also discounted the likelihood of a false flag operation, which attempts to trick researchers or targets into thinking a hack was carried out by some other group. Had Turla been trying to frame OilRig, it would have used OilRig tools and infrastructure exclusively, rather than the combination observed in the hack of the Middle Eastern government's network.
The theory that seems most plausible, the researchers said, is that Turla knew OilRig had already hacked the network of the Middle Eastern target. In later deciding to go after the same target itself, Symantec speculates, Turla piggybacked on existing access of OilRig.
In an interview, Wrolstad, the Symantec researcher, said:
We speculate, but we really can’t confirm, that the purpose of the [OilRig] network infrastructure was to gain that initial foothold. This has been discussed in the community at conferences, that a great way for a group to gain initial access to their victim organization would be to find somebody that already has access to the organization you’re interested in, compromise them, and go out to all the different victims that they have. You can save yourself a lot of trouble by doing that.
It’s been discussed but never before observed, and that was one of the reasons we wanted to document it. The thing that people have talked about, now we have evidence that it happened.
Bad opsec
A theory that’s based on OilRig suffering from a lapse of what researchers call operational security would also be consistent with a recent leak by an unknown party that dumped vast amounts of the group’s code and tools. While it’s possible the leak came from an OilRig insider, Brandon Levene, head of applied intelligence at the security firm Chronicle, said his analysis of the published material leads him to believe it’s the work of outsiders.“It's likely an OilRig controlled staging server was somehow compromised by an outsider," he wrote in an email. "I'd be extremely surprised if the leak(s) were native Iranians. I've seen some linguistic reports that highlight the construction of the messages in Farsi that seem to support this, but there really is no confirmation.”
Symantec researchers, for their part, say they can’t be certain their theory is correct. In the interest of completeness, their report lists their hypothesis (listed as No. 2 below) as only one of four possibilities:
1. False flag: [Turla] does have a track record of using false flag tactics to throw investigators off the scent. However, if this was a genuine attempt at a false flag operation, it begs the question of why it also used its own infrastructure to communicate with other machines on the victim’s network, in addition to using tools that could be traced back to [Turla].
2. Means of intrusion: It is possible that [Turla] wanted to compromise the target organization, found out that [OilRig] had already compromised its network, and hijacked [OilRig]’s own infrastructure as a means of gaining access. Symantec did not observe the initial access point, and the close time frame between [Turla]-observed activity on the victim’s network and its observed use of [OilRig] infrastructure suggests that [Turla] may have used the [OilRig] infrastructure as an initial access point.
3. Mimikatz variant belonged to [OilRig]: There is a possibility that the version of Mimikatz downloaded by the [OilRig] infrastructure was actually developed by [OilRig]. However, the compilation technique and the fact that the only other occasion it was used was linked to [Turla] works against this hypothesis. The fact that [Turla] also appeared on the victim’s network around the same time this version of Mimikatz was downloaded would make it an unlikely coincidence if the tool did belong to [OilRig].
4. Opportunistic sowing of confusion: If a false flag operation wasn’t planned from the start, it is possible that [Turla] discovered the [OilRig] intrusion while preparing its attack and opportunistically used it in the hopes of sowing some confusion in the mind of the victim or investigators. Based on recent leaks of [OilRig] internal documents, its Poison Frog control panel is known to be vulnerable to compromise, meaning it may have been a relatively trivial diversion on the part of [Turla] to hijack [OilRig]’s infrastructure. A compromise conducted by one threat actor group through another's infrastructure, or fourth-party collections, has been previously discussed in a 2017 white paper by Kaspersky researchers.
The white paper speculates on three instances that may support one hacking group compromising the infrastructure of another. The details, however, are extremely sparse. The instances are:
- In 2014, a site infected by hacking group Energetic Bear in hopes of compromising targets who visited it was modified to include an HTML tag that would log visitors’ IP addresses with a remote server controlled by another, undisclosed party.
- A “mothership” server belonging to threat group NetTraveler contained a backdoor planted by another threat actor intent on maintaining prolonged access to the NetTraveler infrastructure for their stolen data.
- In 2016 a Korean-speaking threat actor named DarkHotel compromised a site located at scarcroft.net with what at the time was a zeroday vulnerability in Adobe’s Flash media player. Later, another group the researchers later came to call ScarCruft infected the same scarcroft.net site with a different Flash zeroday.
"While this represents an immediate failure for the victim intelligence service, the tragedy doesn’t end there,” researchers Juan Andrés Guerrero-Saade and Costin Raiu, both at Kaspersky Lab at the time, wrote in the paper titled Walking in your enemy’s shadow: when fourth-party collection becomes attribution Hell. “Attackers can then go on to adopt the victim threat actor’s toolkit and infrastructure, leveraging their data and access, and perpetrating attacks in their name.”
Misidentifying hacking groups might also prove costly to the parties who are breached, since the victims may fail to accurately assess the full scope of the damage they have sustained.
“In the case we’re looking at, we have a very capable threat actor who creates a lot of redundant overlapping access within a network, and then a less capable actor,” Alexandrea Berninger, a senior cyber intelligence analyst at Symantec, said in an interview. "One can imagine that if [you think] you’re defending against a less capable actor you won’t remove all evidence and [the more capable group] will be able to retain some kind of access.”
reader comments
41