Google’s Chrome browser is undergoing a major architectural change to enable a protection designed to blunt the threat of attacks related to the Spectre vulnerability in computer processors. If left unchecked by browsers or operating systems, such attacks may allow hackers to pluck passwords or other sensitive data out of computer memory when targets visit malicious sites.
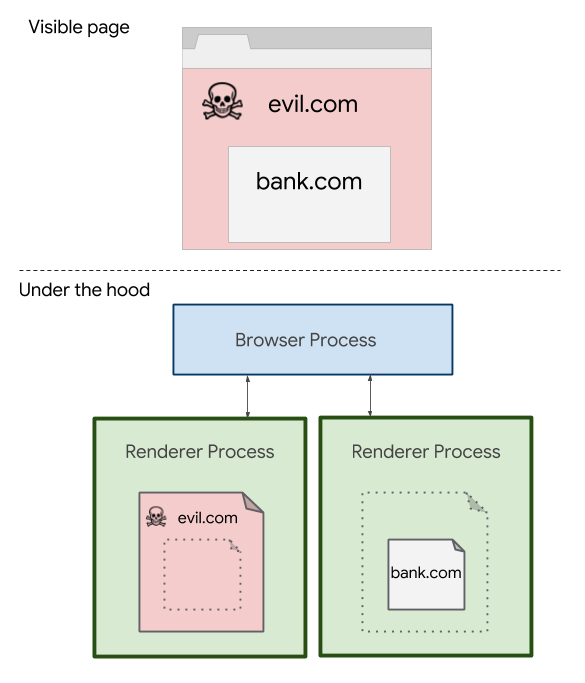
Site isolation, as the mitigation is known, segregates code and data from each Internet domain into their own "renderer processes," which are individual browser tasks that aren't allowed to interact with each other. As a result, a page located at arstechnica.com that embeds ads from doubleclick.net will load content into two separate renderer processes, one for each domain. The protection, however, comes at a cost. It consumes an additional 10 to 13 percent of total memory. Some of the performance hit can be offset by smaller and shorter-lived renderer processes. Site isolation will also allow Chrome to re-enable more precise timers, which Google and most other browser makers disabled earlier this year to decrease chances of successful attacks.
Site isolation has been available in Chrome as an optional mitigation since early this year, but starting with version 67, it's being enabled by default for 99 percent of users. Google is leaving it off for the other 1 percent so engineers can monitor and improve performance. The protection is also being enabled in the Chrome desktop. For performance reasons, it isn't available in Chrome for Android for the time being.
An impressive feat
The mitigation is an impressive engineering feat that's designed to lessen the damage of attacks that exploit a new class of vulnerability that came to light in January. Dubbed Spectre, the attack abuses a CPU optimization technique known as speculative execution so that it can obtain passwords, cryptographic keys, and other memory-resident data that normally should be off limits to untrusted pieces of code. The flaw has represented a serious threat to people browsing websites because individual pages often serve JavaScript from multiple domains that run in the same process. That leaves open the possibility that a malicious ad might steal sensitive user data belonging to a site hosting the ad, a hack that would violate a Web security cornerstone known as the same origin policy.



 Loading comments...
Loading comments...
