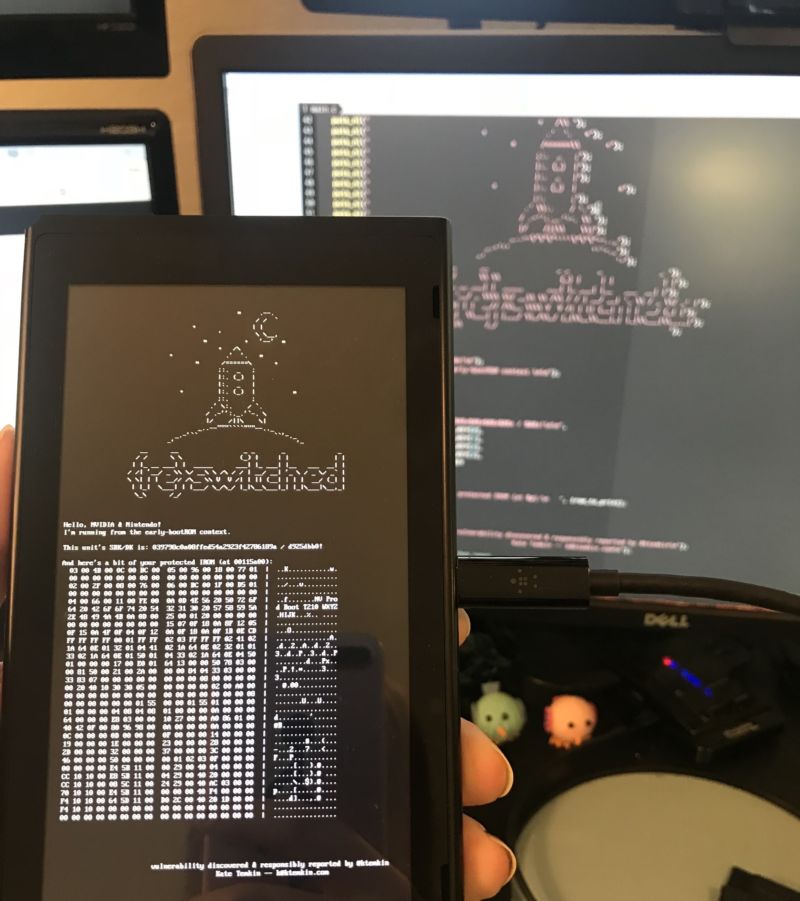
A newly published "exploit chain" for Nvidia Tegra X1-based systems seems to describe an apparently unpatchable method for running arbitrary code on all currently available Nintendo Switch consoles. Hardware hacker Katherine Temkin and the hacking team at ReSwitched released an extensive outline of what they're calling the Fusée Gelée coldboot vulnerability earlier today, alongside a proof-of-concept payload that can be used on the Switch.
"Fusée Gelée isn't a perfect, 'holy grail' exploit—though in some cases it can be pretty damned close," Temkin writes in an accompanying FAQ.
The exploit, as outlined, makes use of a vulnerability inherent in the Tegra X1's USB recovery mode, circumventing the lock-out operations that would usually protect the chip's crucial bootROM. By sending a bad "length" argument to an improperly coded USB control procedure at the right point, the user can force the system to "request up to 65,535 bytes per control request." That data easily overflows a crucial direct memory access (DMA) buffer in the bootROM, in turn allowing data to be copied into the protected application stack and giving the attacker the ability to run arbitrary code.
On the Switch, the hardest part of the exploit seems to be forcing the system into USB recovery mode. To do this without opening the system requires shorting out a certain pin on the right Joy-Con connector (the bit on the side of the system where the Joy-Con clicks into place). The hacking team at Fail0verflow tweeted a picture of a small plug-in device that can apparently provide this short-out easily, and the team joked that a simple piece of wire from the hardware store can do so today. Temkin also tweeted a picture suggesting that simply exposing and bending the pin in question would also work.
Unpatchable?
What makes this exploit particularly worrisome for Nintendo and other Tegra vendors is that it apparently can't be fixed via a simple downloadable patch; the flawed bootROM in question can't be modified once the Tegra chip leaves the factory. That's an important security measure if the bootROM itself is secure but a big problem if the bootROM is exploited, as seems to be the case here (Nintendo and Nvidia were not immediately available to respond to a request for comment).
As Temkin writes, "Unfortunately, access to the fuses needed to configure the device's ipatches was blocked when the ODM_PRODUCTION fuse was burned, so no bootROM update is possible. It is suggested that consumers be made aware of the situation so they can move to other devices, where possible."

That suggestion is unlikely to be of much use to Nintendo, which has already shipped more than 14.8 million apparently vulnerable Switch systems to the public. Previous software-level exploits of Nintendo systems (including one for the Switch) could be mitigated via downloable system updates, which Nintendo attempts to force on users by making them a requirement for new software and access to Nintendo's online servers.
That won't be useful for a chip-level bootROM exploit like this. But Nintendo isn't completely powerless in this situation. Even if and when the exploit is spread widely, Nintendo may still be able to detect "hacked" systems when they sign on to Nintendo's servers. The company could then ban those systems from using the Switch's online functions. Nintendo did something similar when it detected early pirated copies of Pokémon Sun & Moon on the Nintendo 3DS. While the potential to aid software pirates is likely of primary concern to Nintendo, there are plenty of legal and handy reasons to make use of an exploit like this. We noted last October how many Switch users seem eager to hack their consoles so they can back up their internal save data to an SD card and protect themselves from complete loss in the case of a broken system.Why now?
Right now, the general public's use of this exploit is limited to a "proof of concept" python program and payload that can be used to display usually protected information from the Switch's boot instruction ROM (this method requires tethering the Switch to a computer via USB, but Temkin suggests in the FAQ that future payloads will allow data to be loaded from the Switch's SD card). Fuller details of how to use the exploit will be published on June 15, Temkin writes, adding on Twitter that "guides and information so you can use it too are forthcoming." And work continues on a custom Switch bootloader called Atmosphère which will apparently take advantage of the exploit to run.
In the FAQ, Temkin says she has previously notified Nvidia and vendors like Nintendo about the existence of this exploit, providing what she considers an "adequate window [for Nvidia] to communicate with [its] downstream customers and to accomplish as much remediation as is possible for an unpatchable bootROM bug."
That said, Temkin writes that she's publicizing the exploit now in part because of "the potential for a lot of bad to be done by any parties who independently discover these vulnerabilities." There are also hints that other groups were threatening to publish a similar exploit ahead of Team ReSwitched's planned summer rollout, forcing today's "early" disclosure.
The release also seems to be partially a response to Team Xecuter, a separate team that is planning to sell a modchip exploit that can allow for similar code execution on the Switch. Temkin writes that she's opposed to Xecuter's explicit endorsement of piracy and efforts "to profit from keeping information to a few people."
While this is the first public disclosure of this low-level method for hacking the Switch, there's ample evidence that many other hackers had independently discovered similar methods in their own research. In fact, this kind of exploit appears to have been key to last September's effort to discover a method to unlock a copy of NES Golf that was hidden on every Switch console.As Switch hacker smealum tweeted earlier today, "seemingly everyone had everything for months—that it remained 'secret' so long is kinda incredible."
[Update: Shortly after this piece went live, Fail0verflow alleged that it had been holding to "a 90-day responsible disclosure window for ShofEL2 ending on April 25. Since another person published the bug so close to our declared deadline, we're going to wait things out. Stay tuned." That update also included a screen of the Dolphin emulator apparently running Nintendo's Legend of Zelda: Wind Waker on a Nintendo Switch.]
[Further update: When it rains, it pours. Fail0verflow has now released its own ShofEL2 Tegra X1 bootROM exploit alongside a Nintendo Switch Linux loader, ahead of that planned April 25 launch. While the command-line steps to run the exploit don't seem too onerous for the technically inclined, the group warns: "it's stupidly easy to blow up embedded platforms like this with bad software (e.g. all voltages are software-controlled). We already caused temporary damage to one LCD panel with bad power sequencing code. Seriously, do not complain if something goes wrong."]
reader comments
126