For years, executives at France-based Ledger have boasted their specialized hardware for storing cryptocurrencies is so securely designed that resellers or others in the supply chain can't tamper with the devices without it being painfully obvious to end users. The reason: "cryptographic attestation" that uses unforgeable digital signatures to ensure that only authorized code runs on the hardware wallet.
"There is absolutely no way that an attacker could replace the firmware and make it pass attestation without knowing the Ledger private key," officials said in 2015. Earlier this year, Ledger's CTO said attestation was so foolproof that it was safe to buy his company's devices on eBay.
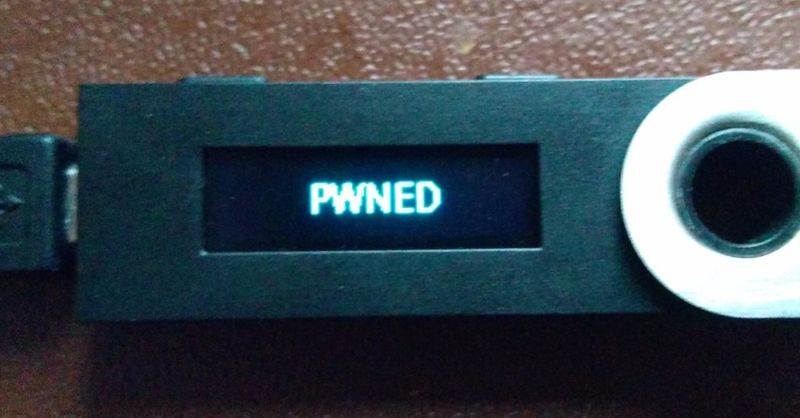
On Tuesday, a 15-year-old from the UK proved these claims wrong. In a post published to his personal blog, Saleem Rashid demonstrated proof-of-concept code that had allowed him to backdoor the Ledger Nano S, a $100 hardware wallet that company marketers have said has sold by the millions. The stealth backdoor Rashid developed is a minuscule 300-bytes long and causes the device to generate pre-determined wallet addresses and recovery passwords known to the attacker. The attacker could then enter those passwords into a new Ledger hardware wallet to recover the private keys the old backdoored device stores for those addresses.
Using the same approach, attackers could perform a variety of other nefarious actions, including changing wallet destinations and amounts for payments so that, for instance, an intended $25 payment to an Ars Technica wallet would be changed to a $2,500 payment to a wallet belonging to the backdoor developer. The same undetectable backdoor works on the $200 Ledger Blue, which is billed as a higher-end device. Variations on the exploit might also allow so-called "evil maid attacks," in which people with brief access to the device could compromise it while they clean a user's hotel room.
Two weeks ago, Ledger officials updated the Nano S to mitigate the vulnerability Rashid privately reported to them in November. In the release notes for firmware version 1.4.1, however, Ledger Chief Security Officer Charles Guillemet stressed the vulnerability was "NOT critical." In a deeper-dive into the security fix published Tuesday, Guillemet said the "attack cannot extract the private keys or the seed," an assertion that Rashid has publicly challenged as incorrect.
Guillemet also said Ledger can detect backdoored wallets if they connect to the Ledger server using a device manager to load applications or update the firmware. He said he had no estimate when the same vulnerability in Ledger Blue would be patched. "As the Blue has been distributed almost exclusively through direct sales, the probability to run the 'shady reseller scam' is negligible," he said. Meanwhile, the company post saying there is "absolutely no way" firmware can be replaced on Ledger devices remains.
A fundamentally hard problem
Rashid said he has yet to verify that this month's Nano S update fully neutralizes his proof-of-concept backdoor exploit as claimed by Ledger. But even if it does, he said he believes a key design weakness in Ledger hardware makes it likely his approach can be modified so that it will once again work. Specifically, the Ledger Blue and Nano S rely on the ST31H320 secure microcontroller from STMicroelectronics to provide the cryptographic attestation that the device is running authorized firmware. The secure microcontroller doesn't support displays, USB connections, or high-throughput communications, so Ledger engineers added a second general-purpose microcontroller, the STM32F042K6, to serve as a proxy.
The secure microcontroller, which Ledger calls the Secure Element, communicates directly with the general-purpose microcontroller, which Ledger calls the MCU. The MCU, in turn, communicates with the rest of the hardware wallet, including its USB host, built-in OLED display, and device buttons users press to control various wallet functions. In a nutshell, Rashid's exploit works by replacing the genuine firmware with unauthorized code while at the same time causing the MCU to send the Secure Element the official firmware image.
Matt Green, a Johns Hopkins University professor specializing in encryption security, has reviewed Rashid's research. Green told Ars the dual-chip design makes him skeptical that this month's update permanently fixes the weakness Rashid exploited.
"Ledger is trying to solve a fundamentally hard problem," he explained. "They need to check the firmware running on a processor. But their secure chip can't actually see the code running on that processor. So they have to ask the processor to supply its own code! Which is a catch-22, since that processor might not be running honest code, and so you can't trust what it gives you. It's like asking someone who may be a criminal to provide you with their full criminal record—on the honor system."
The difficulty of solving the problem is in stark contrast to the confidence Ledger marketers profess in guaranteeing the security of the devices. In addition to the tamper-proof assurances mentioned earlier, the company includes a leaflet with each device. It reads: "Did you notice? There is no anti-tampering sticker on this box. A cryptographic mechanism checks the integrity of your Ledger device's internal software each time it is powered on. The Secure Element chip prevents any interception or physical replacement attempt. Ledger devices are engineered to be tamper-proof."

Creative and devastating
To be fair, Ledger engineers took steps to prevent the MCU from being capable of misrepresenting to the Secure Element the code that's running on the device. The Secure Element requires the MCU to pass along the entire contents of its flash memory. At the same time, the MCU has a relatively limited amount of flash memory. To sneak malicious code onto a hardware wallet, the MCU must, in theory, store the official Ledger firmware and the malicious code. Generally speaking, the storage capacity of the MCU should prevent this kind of hack from working.
Rashid got around this challenge after noticing that the MCU stores both a bootloader and firmware and that the certain types of software functions called "compiler intrinsics" in these separate programs were identical. He then removed the intrinsics in the firmware and replaced them with his ultra-small malicious payload. When the Secure Element asked the MCU for its flash contents—which, of course, included the unauthorized firmware—Rashid's hack pieced together a legitimate image by removing the malicious code and replacing it with the legitimate intrinsics from the bootloader. As a result, the Secure Element mistakenly verified the backdoored firmware as genuine.
The result was a device that generated wallet addresses and recovery passwords that weren't random but, rather, were entirely under the control of the backdoor developer. The 24 passwords, which technically are known as recovery seed, are used in the event a hardware wallet is lost or broken. By entering the seed into a new device, the wallet addresses' private keys stored in the old device are automatically restored.
A video accompanying Rashid's blog post shows a device displaying the word "abandon" for the first 23 recovery passwords and "art" for the remaining one. A malicious backdoor could provide a recovery seed that appeared random to the end user but was entirely known to the developer.
"He's carving up the firmware in a really efficient way to fit it into a tiny amount of space to pull off the attack here," said Kenn White, an independent researcher who reviewed Rashid's research before it was published. "It's well done, it's clever, it's creative, and it's devastating."
Rashid told Ars that it might have been possible for his backdoor to do a variety of other nefarious things. He also said the weaknesses could be exploited in evil-maid scenarios in which someone has brief access to the device and possibly by malware that infects the computer the device is plugged into. Researchers are usually quick to point out that physical access and malware-infected computers are, by definition, compromises on their own and hence shouldn't be considered a valid means for compromising the hardware wallets. The chief selling point of hardware wallets, however, is that they protect users against these fatal events.
Rashid declined to provide much personal information to Ars other than to say he's 15, lives in the south part of the UK, and is a self-taught programmer. Neither White nor Green said they verified Rashid's age, but they also said they had no reason to doubt it.
"I'd be heartbroken if he wasn't 15," Green said. "He's one of the most talented 15-year-olds I've ever talked to. Legitimate hacking genius. If he turns out to be some 35-year-old, he'll still be legit talented, but my faith in humanity will be shaken."
reader comments
120