Data-stealing Qadars Trojan malware takes aim at 18 UK banks

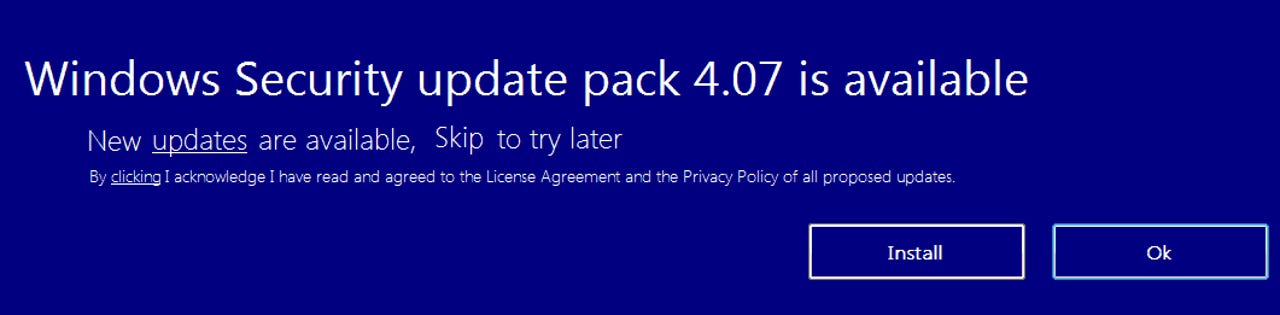
The fake security update used by Qadars.
A three-year-old banking Trojan, believed to be the work of experienced and organised Russian cybercriminals, has now turned its attention to UK banks.
The Qadars Trojan has been active since 2013. Using several different versions, the malware has targeted banks in different regions, beginning with France and the Netherlands during 2013 and 2014, then Australia, Canada, the United States, and the Netherlands during 2015 and 2016.
Security
Now, cybersecurity researchers at IBM X-Force Research -- who last month spotted malware attacking Brazilian banks ahead of the Olympics -- have observed the launch of a fresh version of Qadars and a new infection campaign.
This time, the malware campaign is targeting 18 banks in the UK -- which haven't been named for security reasons -- as well as financial institutions in Germany, Poland, and once again, the Netherlands. UK banks have recently also been targeted by a separate data-stealing Dridex malware campaign.
Qadars historically infects end-points using exploit kits found on compromised hosts, or on domains purchased for the purpose of serving malware. It has also been known to employ botnets, using downloader-type malware to infect victims.
Qadars uses social engineering to help take control of systems and undertake full-scale theft of data, including information from the two-factor authentication systems used by many online banking services. The Trojan is also capable of monitoring all user activity on a device and hijacking text messaging on the victim's mobile phone.
While Qadars predominantly focuses on stealing bank data, it also targets Facebook users, online sports betting users, e-commerce, and others.
The latest version of the malware, Qadars v3, initially appeared in the first quarter of this year and was in regular use by May. Indeed, after only a few months, the authors of the malware had released bug fixes and improvements to the code: these notes are said to be written in Russian and IBM X-Force research analysis suggests that all the code comes from a single source.
Whoever may be behind Qadars, they're thought to be a highly-professional, organised group, as demonstrated by the continual evolution of the malware and the advanced techniques it uses to squeeze as much information out of the victim as possible.
One of those is a privilege-escalation trick which sees Qadars' dropper using social engineering to dupe the user into believing there's a new Windows security update ready to be installed on their system. However, if the victim agrees to install this fake update, it doesn't secure them against anything, but rather does the opposite: it provides Qadars with admin rights to their entire machine -- and potentially any data stored on it.
While the number of incidents involving Qadars is small compared to other Trojans such as GozNym or Dridex -- with the latter arguably the greatest Trojan threat to the financial sector -- the malware is extremely effective, especially as it mainly focuses only on specific regions at one time - hence the rise of attacks against UK banks in the last month.
It's possible that those behind Qadars don't engage in large-scale attacks because they want to remain under the radar and able to carry out focused and less visible operations in order to continue to steal data for profit, rather than for bragging rights like some other hacking groups.
Naturally, acting as large depositories of both money and financial data, banks are a lucrative target for hackers and therefore constantly face persistent and sophisticated cyberattacks.
READ MORE ON CYBERCRIME