Researchers from the Vrije University in the Netherlands have revealed a new version of the infamous Rowhammer attack that is effective in compromising Linux VMs, often used for cloud hosting services.
The Rowhammer attack was discovered two years ago and caused a lot of stir when researchers disclosed it because it showed how, by bombarding a row of memory cells, an attacker could reverse binary zeros into ones and vice versa.
This allowed an attacker to manipulate a computer's memory just by using malware that constantly hammered a row of memory cells, which flipped their bits and influenced nearby memory cells into flipping their bits as well.
Rowhammer attacks evolved across the years
The initial attack was successful against DDR3 memory, but last year, researchers proved that it was also effective against DDR4.
Things took a turn for the worse when researchers demoed Rowhammer attacks via JavaScript, meaning attackers could compromise a computer's memory via the Internet.
Previously, in May 2016, researchers executed a Rowhammer attack against the Edge browser on Windows 10, using a memory deduplication side-channel attack that allowed them to take over the browser and even the OS.
The same team who carried out this research, which was presented at the 37th IEEE Symposium on Security and Privacy, has now returned with a new variation of this attack that they presented last week at the Usenix Security Symposium.
FFS Rowhammer works against Linux VMs
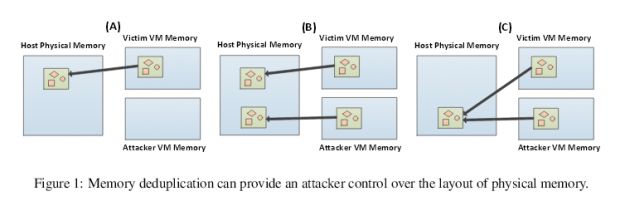
Called Flip Feng Shui (FFS), this is another variation on the Rowhammer attack that also works in conjunction with memory deduplication, a process through which some operating systems free memory slots by finding duplicate entries and merging them together.
In their research called Flip Feng Shui: Hammering a Needle in the Software Stack, the researchers detail Rowhammer attacks on Linux cloud servers.
The attack is basically the same as the Edge scenario, only it's carried out on the memory of a shared Linux-based virtual machines.
The researchers claim that an attacker can buy access to cloud servers co-hosted with their victim, and using an FFS Rowhammer attack, they can gain control of the victim's accounts despite the complete absence of software vulnerabilities.
Because the attacker shares the server with the victim, they can carry out Rowhammer attacks unabated, targeting and creating memory cells that will be selected by the Linux memory deduplication system (KSM). KSM will join these memory cells together, usually into the attacker's memory slot.
"At this stage, FFS already provides the attacker with templated bit flips over the victim’s physical memory pages with known (or predictable) contents," the researchers explain. "The exploitation surface is only subject to the available templates and their ability to reach interesting locations for the attacker."
According to the researchers, this is easy. For their paper, they carried out two proof-of-concept attacks that allowed them to contaminate RSA public keys by one bit, which enabled them to establish SSH connections to the victim's machine, or modify its APT sources and trick the user into installing malicious APT packages.
The problem is not Linux VMs, but cryptographic software
In their work, the attackers successfully targeted Debian and Ubuntu systems. Both projects were informed of the issues.
But while the two Linux-based projects are dealing with the reported problems, the real issue is in the cryptographic software, which they say they were able to corrupt.
"We find that, while dFFS is surprisingly practical and effective, existing cryptographic software is wholly unequipped to counter it, given that 'bit flipping is not part of their threat model,'" the researchers said.
"Even more worryingly, we believe Flip Feng Shui can be used in several more forms and applications pervasively in the software stack, urging the systems security community to devote immediate attention to this emerging threat."

 14 DAY TRIAL //
14 DAY TRIAL //