Malicious websites are exploiting a recently fixed vulnerability in Microsoft's Silverlight application framework to perform drive-by malware attacks on vulnerable visitor devices, a security researcher has determined.
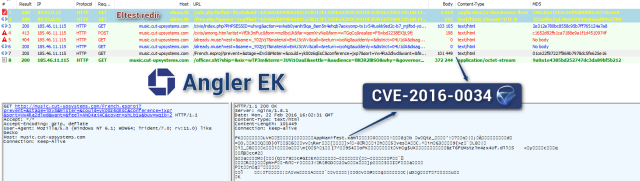
The critical code-execution vulnerability, which Microsoft patched last month, was actively exploited for two years in attack code owned by Italy-based exploit broker Hacking Team. As Ars reported last July, the Silverlight exploit came to light following a hack on Hacking Team's network that exposed gigabytes worth of private e-mails and other data. Researchers with Russian antivirus provider Kaspersky Lab later discovered the vulnerability being exploited in the wild and privately reported it to Microsoft.Now, exploit code for the patched vulnerability is being distributed through Angler, one of several toolkits that criminals use to seed websites with code that carry out drive-by attacks. The Silverlight attack was spotted earlier this week by a researcher who goes by the moniker Kafeine. The vulnerability is indexed as CVE-2016-0034.
Kafeine's post doesn't specify exactly what platforms are being targeted, but Microsoft has been clear that exploits have the ability to remotely execute malicious code on both unpatched Windows and OS X devices. It's also unclear if the Angler exploit was developed by reverse engineering the patch Microsoft released in January or if Angler developers obtained the code already available through Hacking Team.
While Silverlight vulnerabilities aren't nearly as numerous as security bugs in Adobe's Flash or Oracle's Java, Kafeine's discovery shows that the Microsoft framework has the potential to endanger a broad base of people using both Windows and OS X. Readers who can browse the Internet without Silverlight are best off uninstalling it. Everyone else should religiously update it as soon as patches become available. Patched versions are 5.1.41212.0 or higher.
reader comments
62