
It's been quite a few months for the Tor Project. Last November, project co-founder and director Roger Dingledine accused the FBI of paying Carnegie Mellon computer security researchers at least $1 million to de-anonymize Tor users and reveal their IP addresses as part of a large criminal investigation.
The FBI dismissed things, but the investigation in question is a very high-profile matter focused on members of the Silk Road online-drug marketplace. One of the IP addresses revealed belonged to Brian Farrell, an alleged Silk Road 2 lieutenant. An early filing in Farrell's case, first reported by Vice Motherboard, said that a "university-based research institute" aided government efforts to unmask Farrell.
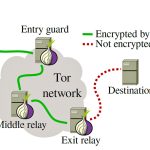
That document fit with Ars reporting from January 2015, when a Homeland Security search warrant affidavit stated that from January to July 2014, a “source of information” provided law enforcement “with particular IP addresses” that accessed the vendor-side of Silk Road 2. By July 2015, the Tor Project managed to discover and shut down this sustained attack. But the Tor Project further concluded that the attack resembled a technique described by a team of Carnegie Mellon University (CMU) researchers who a few weeks earlier had canceled a security conference presentation on a low-cost way to deanonymize Tor users. The Tor officials went on to warn that an intelligence agency from a global adversary also might have been able to capitalize on the vulnerability.
As this high-stakes situation continued to play out, the Tor Project was also looking for help. Faced with an increased demand and more government scrutiny in the wake of the Snowden leaks, 2015 saw Tor engage in a five-month search for a new executive director, someone who could "be the face and voice of the organization, to educate the public about privacy and encourage wider adoption of its tools, and could court donors to help sustain the organization and fund development of its tools," as Wired put it. And in December, Tor ended its year by hiring Shari Steele, previously the EFF executive director for 15 years.







 Loading comments...
Loading comments...
