Over the past decade, there's been a privacy arms race between unscrupulous website operators and browser makers. The former wield an ever-changing lineup of so-called zombie cookies that can't be easily deleted and attacks that sniff thousands of previously visited sites, while browser makers aim to prevent such privacy invasions by closing the design weaknesses that make them possible. Almost as soon as one hole is closed, hackers find a new one.
Over the weekend, a researcher demonstrated two unpatched weaknesses that Web masters can exploit to track millions of people who visit their sites. Taken together, the attacks allow websites to compile a list of previously visited domains, even when users have flushed their browsing history, and to tag visitors with a tracking cookie that will persist even after users have deleted all normal cookies. Ironically, the techniques abuse relatively new security features that are already built into Google Chrome and Mozilla Firefox and that may make their way into other mainstream browsers in the future.
The history-sniffing attack works against people who visit sites that use HTTP strict transport (HSTS). The specification allows websites to instruct browsers to connect only when an encrypted HTTPS connection is available and to reject any attempts to use an unsecured HTTP link. The measure, which is used by banks, cloud services, and other sensitive sites, is designed to prevent downgrade attacks, in which a hacker with the ability to tamper with traffic passing between an end user and server resets an HTTPS connection to use HTTP so the data isn't protected against snooping or modification.
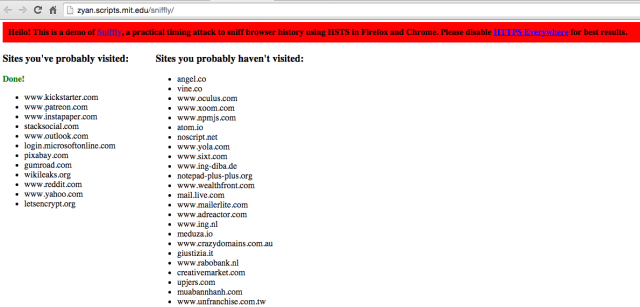
At last weekend's Toorcon security conference in San Diego, independent researcher Yan Zhu demonstrated how websites can abuse HSTS protections to figure out other sites a visitor has previously connected to. The attack works by embedding non-existent images from HSTS-protected sites. The unscrupulous website then uses JavaScript to measure how long it takes for an error to register. If the user has visited the HSTS site before, the error will occur within a few milliseconds. If it takes longer for the error to register, the attacker can determine that the site has never been visited before.
Zhu has developed a proof-of-concept attack site that works with both the Chrome and Firefox browsers. She said the code could probably be modified to work against other browsers. She has also posted the source for her exploit, which she has dubbed Sniffly. A video of her presentation is here.
A similar vulnerability was reported to Google developers no later than last November, but at the time, they said they had no plans to fix it and cited the "futility of preventing origin-level leakage."
Zombie cookies rise again
At the same Toorcon talk, Zhu also described a way a website can track Google Chrome users even when they delete cookies after every visit. Instead of abusing HSTS, the supercookie technique exploits weaknesses in a separate security measure known as HTTP public key pinning (HPKP). Also known as certificate pinning, the measure is designed to protect against certificate forgeries by allowing websites to specify the specific HTTPS credentials that a browser should accept when negotiating all encrypted connections in the future. The official specification allows websites to pin multiple certificates to a browser.
Unscrupulous sites can abuse the standard by pinning text that's unique to each visitor. The site can then read the text on subsequent visits and use the unique text the same way it would use a browser cookie to track the user's site habits. Unlike a cookie, however, the certificate pin will remain intact even after cookies are deleted.
To delete the pins in Chrome, users can type chrome://net-internals/#hsts into the address bar and delete specific domain names they know have set certificate pinning. But there's no way for users to see a full list of all such sites. Another way to delete pins in Chrome is to navigate to preferences and choose "clear browsing data since the beginning of time," but this move will come at the expense of the convenience many people find from having this data stored.
So far, Chrome and Firefox are the only two browsers that are believed to be compatible with certificate pinning. But according to Mozilla, Firefox doesn't yet support certificate-pinning reporting. So while the attack currently appears to work only against Chrome users, it will likely work against a much larger base should other browsers adopt the antiforgery measure.In some respects, the effects of these two browser fingerprinting techniques are less severe than early ones. The history-sniffing attack, for instance, records only the domain and subdomains rather than full URLs. What's more, it tracks only visits to HSTS-protected sites, although that limitation will likely grow less restrictive over time as the specification becomes available on more and more sites. The attack is also slow and generates a large number of false positives, especially if people use the HTTPS Everywhere browser plugin, but such imperfections can likely be overcome with code refinements.
In the past year, researchers have devised other ways to track website visitors who may think the precautions they've taken prevent them from being uniquely identified. One technique abuses a programming interface known as requestAnimationFrame to generate a list of previously visited sites. Another abuses HSTS to create supercookies that can track users browsing in privacy mode. Another one works even against people using the Tor browser to shield their IP address and other identifying features. It measures the minute differences in the way each person presses keys on computer keyboards to profile and track individuals surfing websites.The number of ways to be tracked online is likely to continue growing, no matter what precautions people take.
"There are a lot of browser fingerprinting techniques that people haven't explored yet using new browser features like HPKP HSTS, and content security policy," Zhu told Ars. "Some people say that because of this defending against fingerprinting is a lost cause. I think to some extent, they're probably right."
reader comments
39