Will Windows 10's coming security features win over Windows 7 users?

Microsoft officials have not made much of a case so far as to why Windows 7 users should move to Windows 10.
Yes, the return of a more-or-less familiar Start Menu and the integration of Cortana into the OS are nice, but they aren't the kinds of features that would make users, and especially business users, move off the tried-and-tested operating system that is Windows 7 and is working just fine, thank you.
I'd think the security features that are unique to Windows 10 would be compelling to business customers. To date, and especially recently, Microsoft officials haven't said a whole lot about these features. At least part of the reason may be that a number of the Windows 10 security features that would and should be a selling point with business users have yet to be fully implemented.
Microsoft definitely has talked up Windows Hello, the new biometric authentication technology that will allow users to sign into their Windows 10 devices without a password. New hardware is needed to take advantage of Hello, since it authenticates using fingerprints and facial recognition. Hello is available to users of all of the various Windows 10 editions -- Home, Pro, Enterprise and Education. There are a number of other security features that will be available only to a subset of Windows 10 users.
Yesterday, Microsoft officials went public with the fact that Windows 10 doesn't yet have the promised Enterprise Data Protection and Passport Enterprise functionality that officials touted earlier this year. (If you read carefully between the lines, Microsoft did concede in various places that Windows 10 was missing these pieces, along with the promised Windows Store for Business capability.)
Microsoft is planning to get these features into Windows 10 preview builds some time this month so as to be able to roll them out later this year, presumably as part of the late Fall Threshold 2 release.
But there are other Windows 10 security features Microsoft has done surprisingly little to trumpet.
One is BitLocker drive encryption. Though this feature was part of Windows 7 and is still in Windows 10, Microsoft is broadening the group of users who can get it. With Windows 7, only Ultimate and Enterprise users got BitLocker. With Windows 10, Pro, Enterprise and Education users all get it.
There's more. Here's a chart I found on the Microsoft Download Center that compares Windows 7 vs. Windows 10 security features:
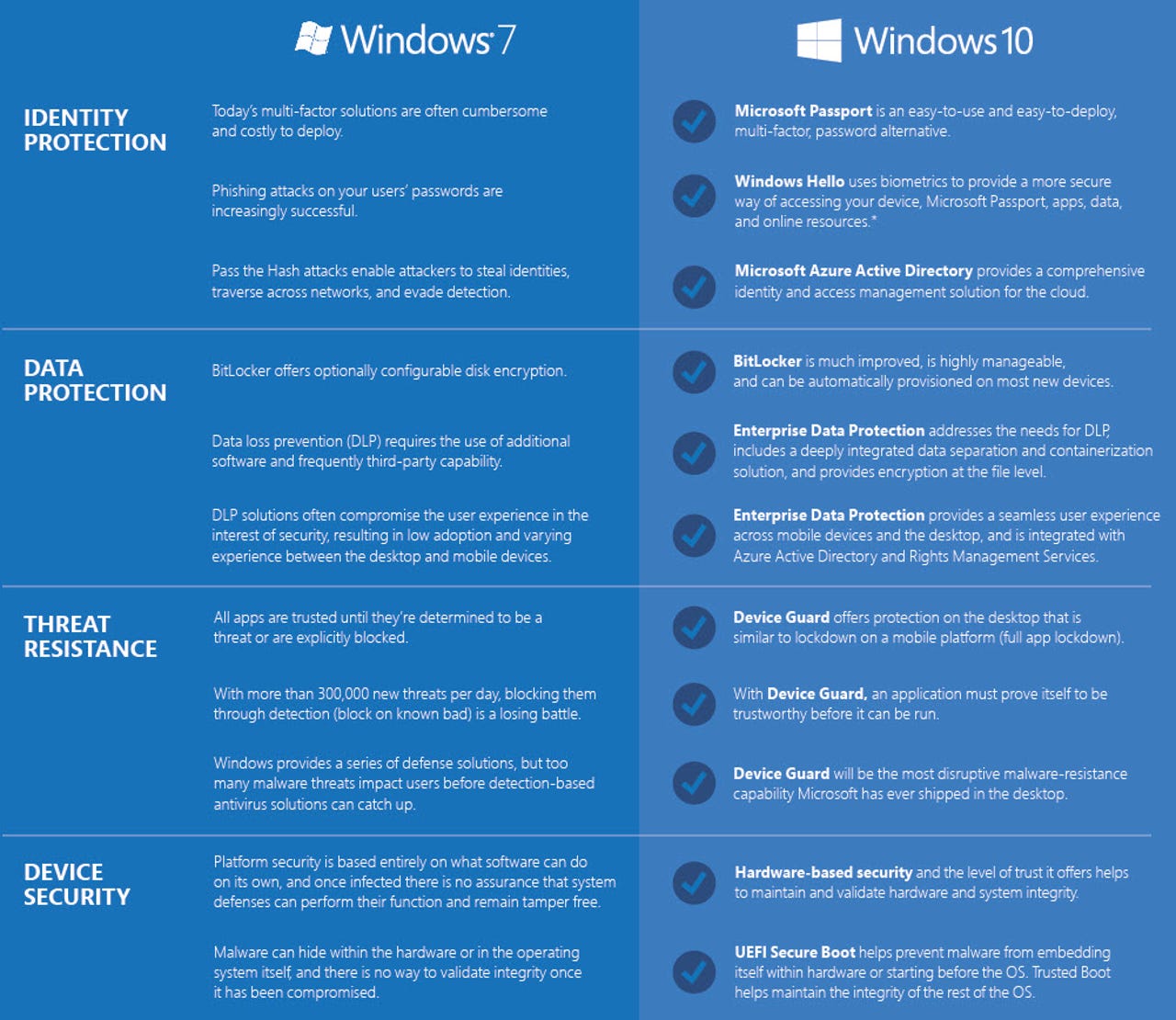
Enterprise Data Protection (EDP) is going to build on the data-loss-prevention capability that's currently part of Windows 7. It goes a step further however, by separating consumer and business data via containers. EDP will be integrated with Azure Active Directory and Rights Management Services. Microsoft is promising EDP will provide "a seamless user experience across mobile devices and the desktop." EDP is going to be available to Windows 10 Pro, Enterprise and Education users.
Microsoft Passport is all about enabling users to more securely log into apps and online and on-premises content without a password. Passport currently supports Microsoft Accounts and Azure Active Directory. While it's already part of Windows 10 Home and Pro, it's not yet baked into Windows 10 Enterprise, Microsoft execs acknowledged yesterday.
Device Guard is another security feature unique to Windows 10, and one about which we've so far heard relatively little. Device Guard provides app lockdown; an application must prove it's trustworthy before it can be run. Microsoft claims Device Guard "will be the most disruptive malware-resistance capability Microsoft has ever shipped in the desktop."
Credential Guard, the sibling service, is all about "isolating secrets." From Microsoft's description of how Credential Guard works:
"Credential Guard isolates secrets that previous versions of Windows stored in the Local Security Authority (LSA) by using virtualization-based security. Prior to Windows 10, the LSA stored secrets used by the operating system. The LSA process in the operating system talks to the isolated LSA by using remote procedure calls. Data stored by using virtualization-based security is not accessible to the rest of the operating system."
Device Guard and Credential Guard will be available to Windows 10 Enterprise and Education users only.
More Windows 10
Going deeper, there's new technology that Microsoft built into the Windows 10 kernel that is enabling Device Guard and Credential Guard. Microsoft recently made available on its Channel 9 site a three-part video series about this technology, known as Isolated User Mode (IUM) that's worth watching. Part 1 starts here.
IUM -- security technology unique to Windows 10 -- introduces the idea of a secure kernel and secure applications, which run in a different address space than the normal kernel.
IUM is grounded in Windows 10's new Virtualization Based Security (VBS) capability, which was formerly known as Virtual Secure Mode. VBS is baked into Windows 10 already. VBS provides hardware-based isolation between Windows functionality running in the VBS environment and the rest of the Windows 10 OS.
"This isolation helps ensure that the processes and data within the VBS environment can't be accessed or tampered with. This type isolation has never existed in Windows prior to Windows 10," according to a Microsoft spokesperson I asked about IUM.
Device Guard uses the VBS environment to prevent its functionality from being tampered with. Device Guard was built to foil hardware-based zero-day attacks on kernel mode. It also goes beyond the security that was built into AppLocker -- which could be tampered with by an attacker who gained administrative privilege, the spokesperson noted.
"Device Guards requires 'signed' policy, which means that only a updated policy that has been signed by a trusted signer can change the app control policy that has been set on the device. Signed policy is critical in our ability to prevent an attacker with admin control form undoing app control policies that would enable the attacker to run untrusted and malicious apps," the spokesperson said.
Credential Guard, meanwhile, uses the VBS environment to prevent theft and misuse of a user's "derived credentials," which can be used in Pass the Hash (PtH) attacks.
With the arrival of the next big update to Windows 10 (Threshold 2) before the year is out, I'm expecting we'll be hearing lots more from Microsoft on the Windows 7 vs. Windows 10 security front. In the interim, it'll be the Windows Insiders who should be talking about how Windows 10's security stacks up.