Recent revelations that Uber stored a sensitive database key on a publicly accessible GitHub page generated its share of amazement and outrage. Some Ars readers called for the immediate termination of the employees responsible or for the enactment of new legal penalties for similar blunders in the future.
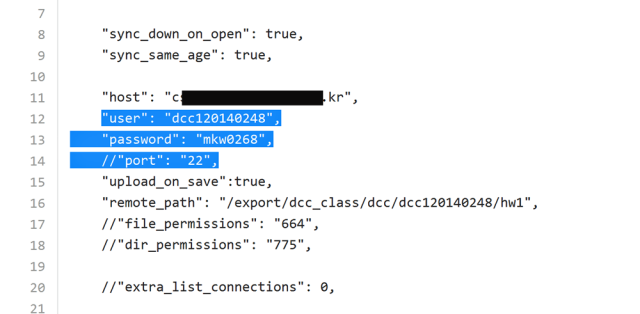
Left out of the discussion was a point Ars first tried to drive home more than two years ago. To wit, GitHub and other public code repositories are awash with personal credentials posted by tens of thousands, or possibly even millions, of people, some of whom work for extremely sensitive organizations. A case in point are GitHub entries that appear to include everything needed to log into many Secure File Transfer Protocol accounts. One GitHub search revealed almost 269,000 entries like the one pictured above, showing the domain name or IP address, username, and password needed to log in to each account. Similar searches generated almost two million entries for WordPress accounts.A quick scan of the results shows that many of them represent no security threat at all, since the password fields are blank or the credentials belong to non-existent accounts or accounts that are accessible only to users already connected to the local network. But a mind-numbingly large percentage of the results appear to provide credentials for accounts on production servers. Whether percentage is 33, 25, or even 10, it's way too high. It wouldn't be surprising if many of the credentials offered shell accounts that ran with highly privileged administrator rights. To protect the careless, this post won't reveal the specific search terms used, even though they are extremely easy for readers figure out on their own or to find on Twitter, in blog posts, or in other venues.
As Ars has reported before, malicious hackers are increasingly favoring Web servers as the target of choice since they offer more computing power and bandwidth compared to more traditionally targeted Windows-based desktops and laptops. Besides increased firepower for waging denial of service attacks, servers often can be used as beachheads to further penetrate company networks. It's hard to imagine criminals aren't already employing automated scripts that regularly trawl GitHub for credentials that can be used for this purpose. Who needs spear phishing and software or Web exploits when the login details are sitting in plain sight?
For obvious legal reasons, Ars didn't test this hypothesis, but Uber's recent admission in court documents suggests it's by no means far-fetched. If a digital key unlocking a database storing driver license numbers of 50,000 Uber drivers can remain on GitHub for six months—as the subpoena Uber filed against GitHub stronly implied—there's no telling what other credentials belonging to other companies are being similarly siphoned up.Readers who are tempted to scoff at Uber's epic blunder have reason to do so. But let's not forget that the ride-sharing service is hardly alone, and this critical mass of carelessness makes the Internet less safe for everyone.
reader comments
61