Though Apple has added additional data security features to the iPhone with every iteration of the OS—including encrypting files on-device for the iPhone 3GS—vulnerabilities still exist. These issues are of particular concern to enterprise users, since sensitive corporate data may exist on any given employee's mobile device. A new vulnerability revealed by security researcher Bernd Marienfeldt, however, shows that all someone needs to get at that data is the latest version of Ubuntu.
Noted iPhone data forensics expert Jonathan Zdziarski demonstrated last year that common hacking tools could remove the data protection features that Apple added with iPhone OS 3.x and the iPhone 3GS. He told Ars that there are ways to get around both the on-device encryption as well as the encrypted backups that can be saved via iTunes. "The only benefit hardware encryption [as implemented] is that it makes wipes faster, by just dropping the [encryption] key," he said. But even the remote wipe feature can be thwarted by removing a device's SIM card.
Marienfeldt's research revealed that standard hacking or jailbreaking tools aren't even needed to get at the data. The latest version of Ubuntu (10.04) will auto mount the flash storage in an iPhone, allowing access to all of the information contained within. Files can be accessed even if a pin code is set.
Zdziarski warned that the way encryption worked on the iPhone could be exploited in this way if a tool allowed the iPhone's file system to be mounted. "The [iPhone OS] kernel decrypts it for you when you ask for files, so you get the decrypted copy," he told Ars last summer.
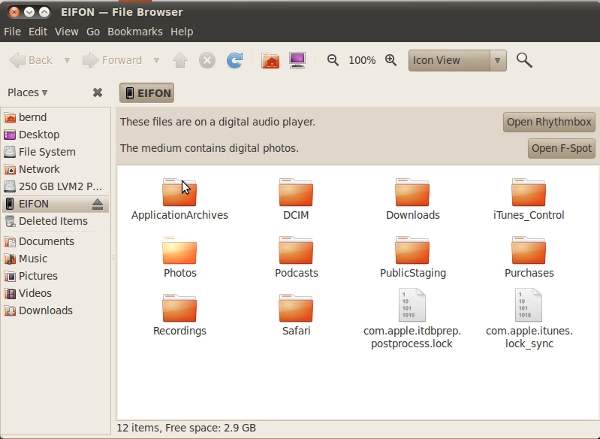
Marienfeldt verified that only the DCIM folder, where images and videos are stored, is accessible on Mac OS X, Windows, and Linux—even older versions of Ubuntu. However, Lucid Lynx will, when set to auto mount USB-based devices, expose the entire filesystem of any iPhone. "This data protection flaw exposes music, photos, videos, podcasts, voice recordings, Google safe browsing database, game contents," Marienfeldt wrote on his blog.
He has shared his findings with Apple, and engineers were able to verify the problem. "Apple could reproduce the described serious issue and believes [it understands] why this can happen but cannot provide timing or further details on the release of a fix," Marienfeldt said.
Of course, knowing that pretty much anyone with Ubuntu installed can get at all of your data is troubling. Marienfeldt noted that this problem is quite serious for enterprise users, especially since companies "rely on the expectation that their iPhone 3GS’s whole content is protected by encryption with a PIN code based authentication in place to unlock it." This is probably true; Steve Jobs recently noted during the iPhone OS 4.0 preview that 80 percent of Fortune 100 companies have employees using iPhones as a work-related mobile device.
AT&T also said that 40 percent of iPhones are now sold to enterprise users. "When the iPhone came out, what most people heard in the first year from '07 to '08 was oh my God, it's not BlackBerry secure; this is not going to work on the enterprise space," AT&T Business Solutions CEO Ron Spears said recently during the Barclays Capital Communications, Media and Technology Conference. "And by the time the 3G came out in ‘08 they had solved about 80 percent of the security issues. By the time the 3GS came out last summer, most CIOs will tell you today they have very few issues around the security that they need provided."
However, this latest example shows that Apple has some work ahead of it to beef up security for its mobile platform. Apple has promised more robust encryption options for iPhone OS 4.0, including giving developers an API to encrypt their applications' data separately. If these new options rely on the same encryption system as current iPhones, though, that won't be enough. Marienfeldt recommends that Apple employ a more robust full disk encryption method, one that requires the PIN code to be entered before the filesystem will mount on any OS.
reader comments
69