Add PHP applications and the WordPress Web platform to the list of wares that may be susceptible to the critical Linux vulnerability known as Ghost.
As Ars reported Wednesday, the flaw resided in a variety of Linux distributions, including Centos/RHEL/Fedora 5, 6, and 7 Ubuntu 12.04, and possibly other versions. The buffer overflow made its way into those distributions through the GNU C Library, specifically in its gethostbyname() and gethostbyname2() function calls. The bug made it possible to execute malicious code by sending malformed data to various applications and services running on vulnerable systems. Proof-of-concept attack code was able to exploit the vulnerability in the Exim mail server, and researchers widely suspected clockdiff, procmail, and pppd were also susceptible.Now, researchers from security firm Sucuri have expanded the list.
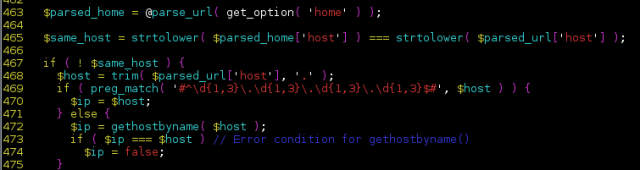
"We also have good reasons to believe PHP applications might also be affected, through its gethostbyname() function wrapper," Sucuri Senior Vulnerability Researcher Marc-Alexandre Montpas wrote in a blog post published Thursday. "An example of where this could be a big issue is within WordPress itself: it uses a function named wp_http_validate_url() to validate every pingback's post URL… and it does so by using gethostbyname(). So an attacker could leverage this vector to insert a malicious URL that would trigger a buffer overflow bug, server-side, potentially allowing him to gain privileges on the server."
Fortunately, there's little evidence Ghost is being maliciously exploited in the wild against mail and Web servers. That's likely because there are several tall hurdles that make successful attacks difficult. Still, attacks only grow more effective over time. Vulnerable Linux installations should be updated as soon as possible, especially if they run any of the apps or services flagged as being vectors for this attack.
reader comments
46